Secret Scanner for Jira and Confluence: CVE-2023–22515 Defense in Depth
Pen Test
NOVEMBER 7, 2023
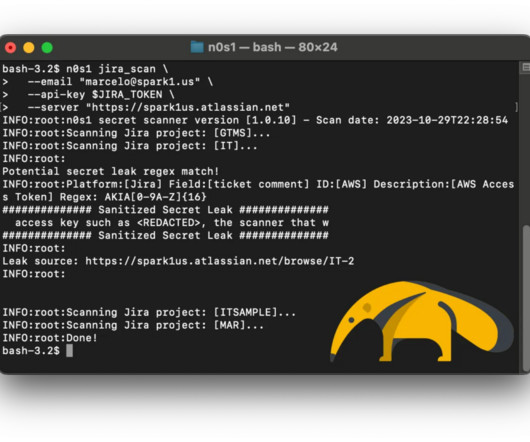
TLDR; Upgrade Confluence to a patched version and employ the open-source security scanner n0s1 to proactively address potential secret leaks. Why do I need a secret scanner? It is a widely recognized best practice for Product Security Engineers to conduct scans of the software codebase in search of potential inadvertent secret leaks.













Let's personalize your content