GoDaddy Employees Used in Attacks on Multiple Cryptocurrency Services
Krebs on Security
NOVEMBER 21, 2020
Fraudsters redirected email and web traffic destined for several cryptocurrency trading platforms over the past week. 13, with an attack on cryptocurrency trading platform liquid.com. “Our security team investigated and confirmed threat actor activity, including social engineering of a limited number of GoDaddy employees.












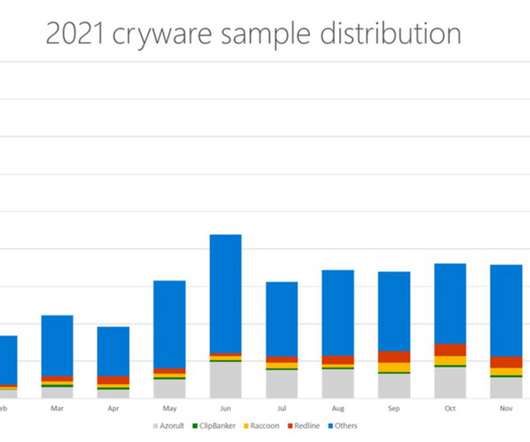



































Let's personalize your content