What Is Encryption as a Service (EaaS)? A Definitive Guide
Heimadal Security
FEBRUARY 3, 2023
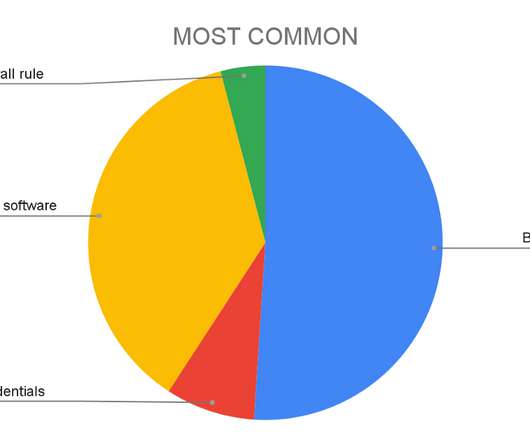
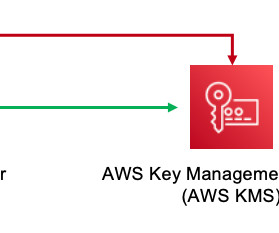
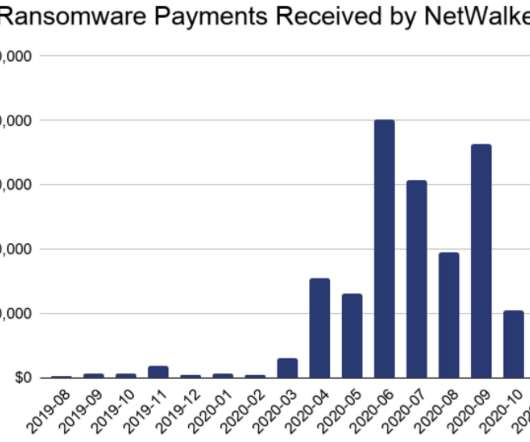
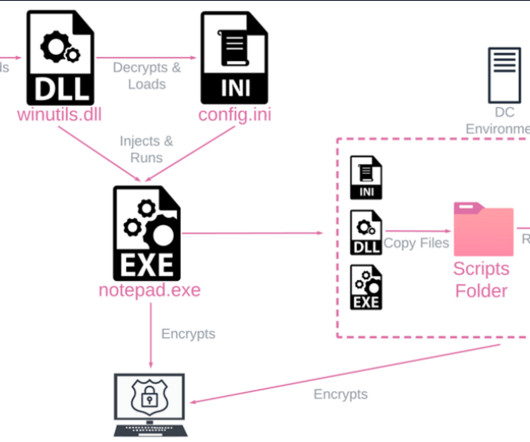
Whether your company is subject to stringent cybersecurity regulatory requirements or you want to strengthen your overall security, encryption as a service is an effective way to protect sensitive data at rest and in transit. And […] The post What Is Encryption as a Service (EaaS)?










































Let's personalize your content