Anton’s Security Blog Quarterly Q4 2021
Security Boulevard
DECEMBER 20, 2021
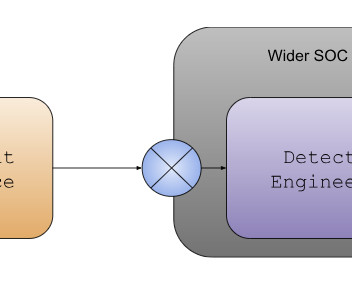
Sometimes great old blog posts are hard to find (especially on Medium ) , so I decided to do a periodic list blog with my favorite posts of the past quarter or so. This covers both Anton on Security and my posts from Google Cloud blog , and our Cloud Security Podcast too ( subscribe ). “Can Can We Have “Detection as Code”?”.
















































Let's personalize your content