Hackers are taking advantage of the interest in generative AI to install Malware
Security Affairs
MAY 3, 2023
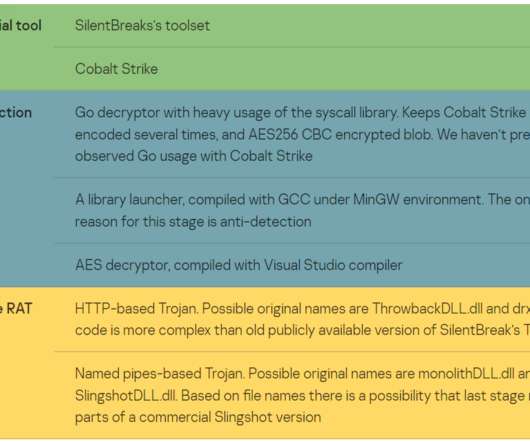
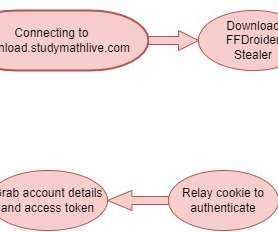
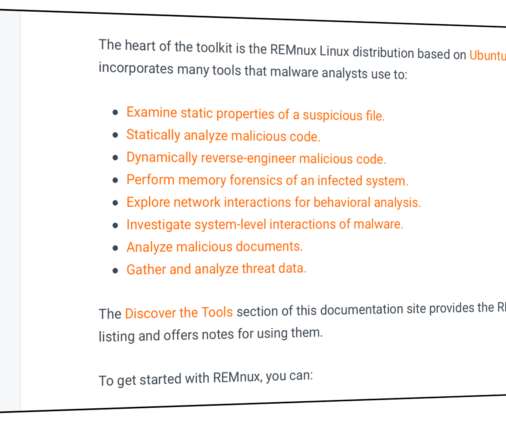
Threat actors are using the promise of generative AI like ChatGPT to deliver malware, Facebook parent Meta warned. Threat actors are taking advantage of the huge interest in generative AI like ChatGPT to trick victims into installing malware, Meta warns. ” reads the Meta’s Q1 2023 Security Reports.




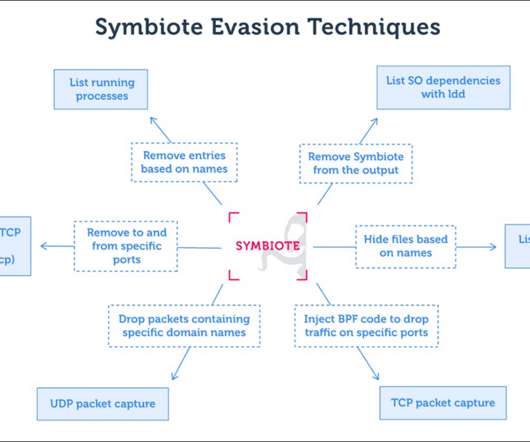

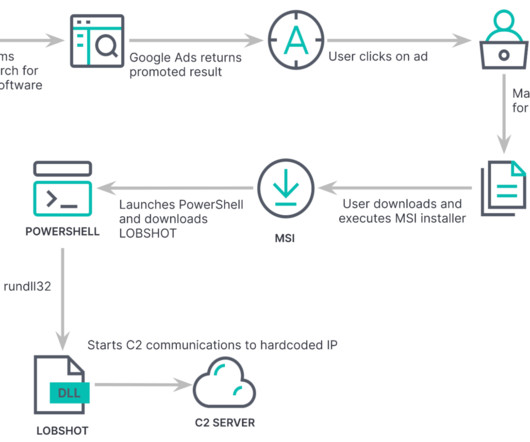
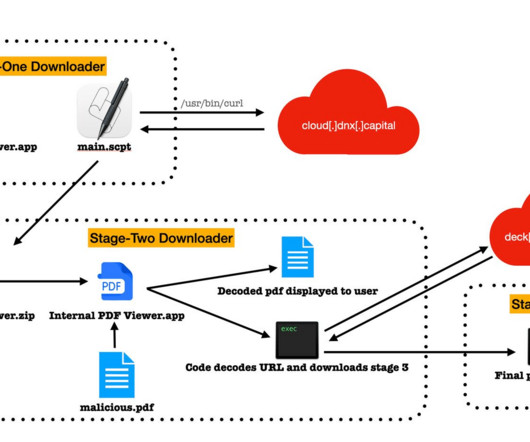

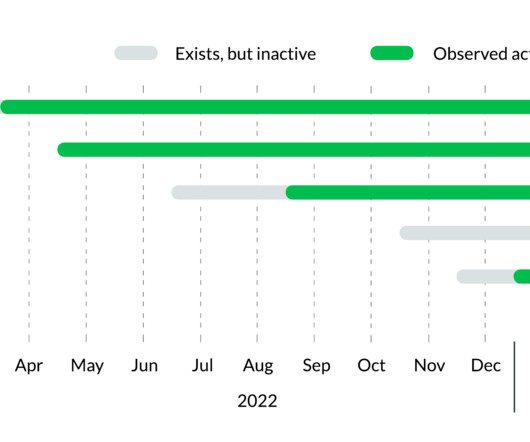


















Let's personalize your content