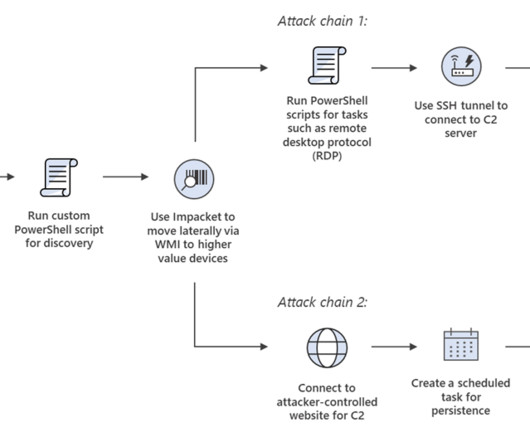
Mitigating Lateral Movement with Zero Trust Access
Cisco Security
MARCH 5, 2024
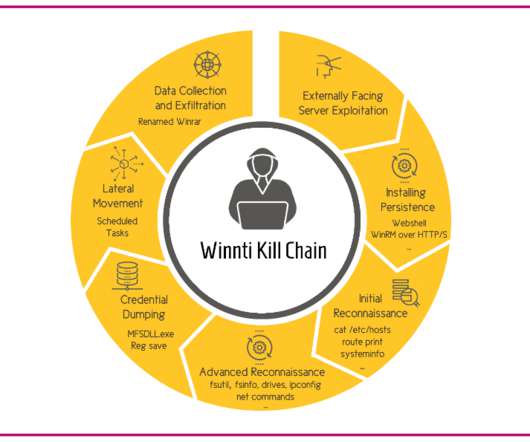
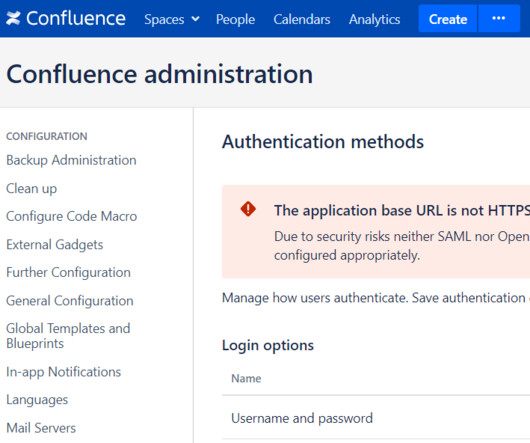
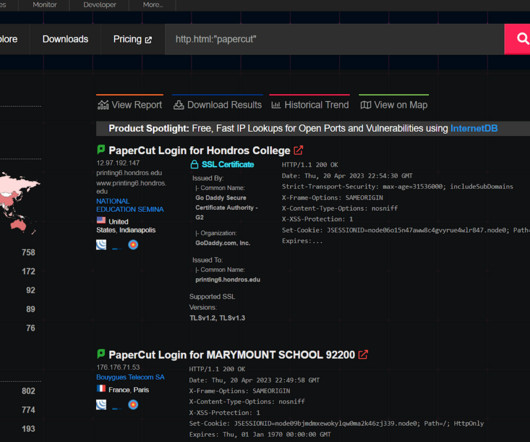
To understand how SSE solutions protect organizations and their… Read more on Cisco Blogs Stop lateral movement in its track with zero trust access. Security service edge (SSE) technology was created to protect remote and branch users with a unified, cloud-delivered security stack.




































Let's personalize your content