Micro-Segmentation: Strengthening Network Security Through Granular Control
Heimadal Security
JULY 14, 2023
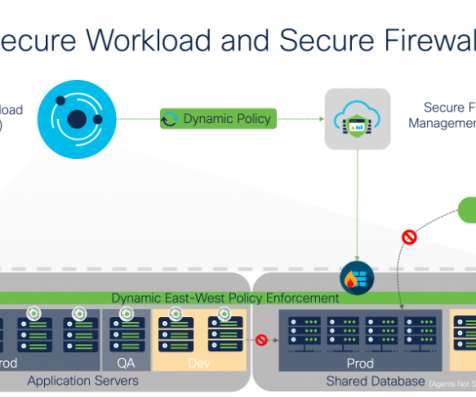
A fundamental component of the ZT […] The post Micro-Segmentation: Strengthening Network Security Through Granular Control appeared first on Heimdal Security Blog. Consequently, a paradigm shift has emerged, giving rise to the Zero Trust (ZT) strategy.































Let's personalize your content