Your All-In Guide to MSP Patch Management Software in 2024 [Template Included]
Heimadal Security
APRIL 15, 2024
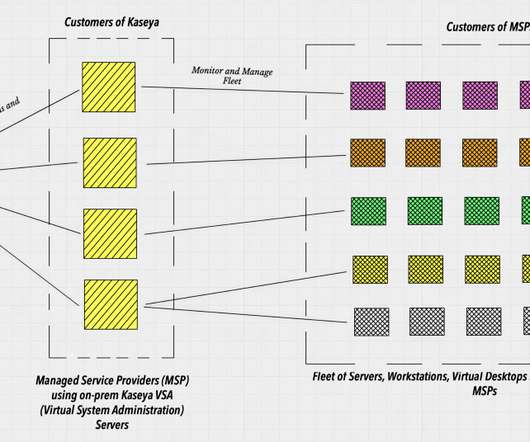
Patch management is one of the most effective, yet overlooked cybersecurity practices to keep your operations safe. And it’s not just me saying it, statistics do too. For example, were you aware that 80% of cyberattacks happen due to unpatched vulnerabilities?




















Let's personalize your content