10 Best Privileged Identity Management Tools (2024)
Heimadal Security
FEBRUARY 1, 2024
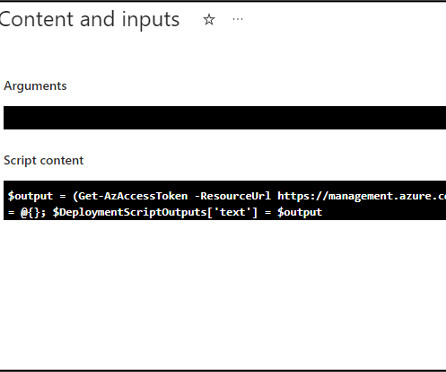
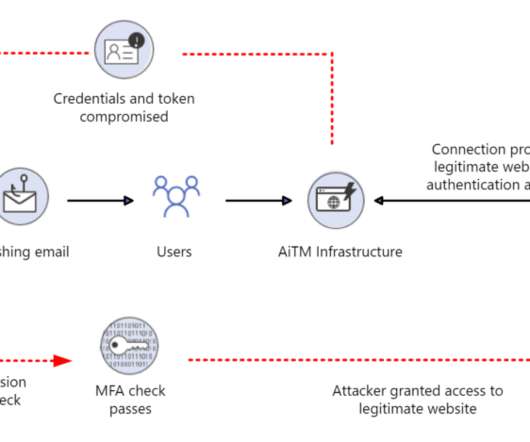
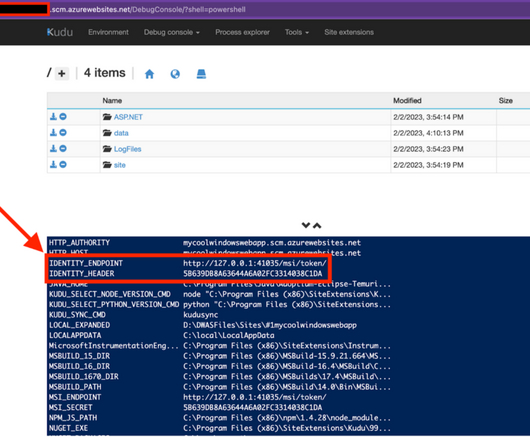
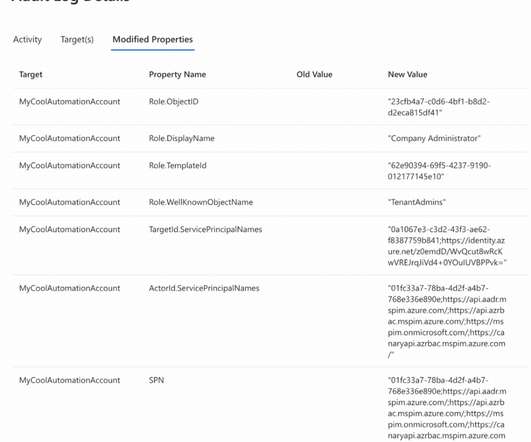
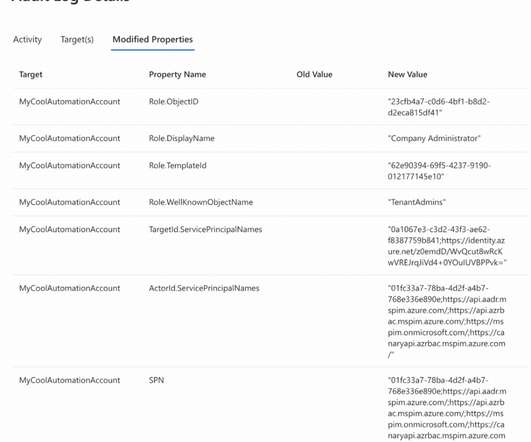
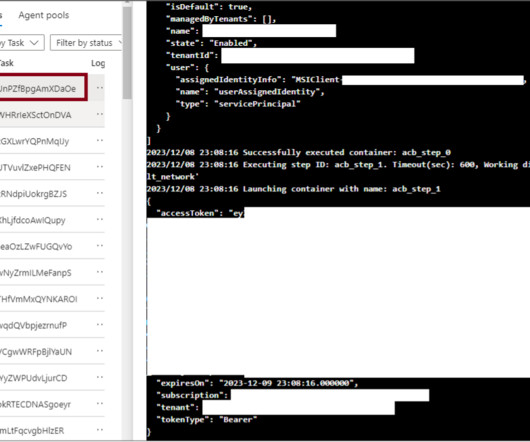
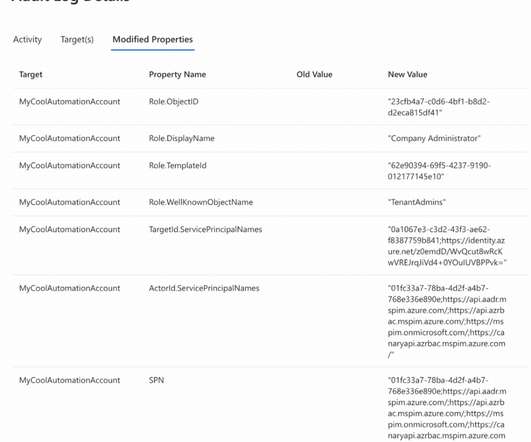
The Importance of Choosing the Right Privilege Identity Management Solution The essence of effective Privileged Identity Management (PIM) lies not in identity or management but in privilege.




























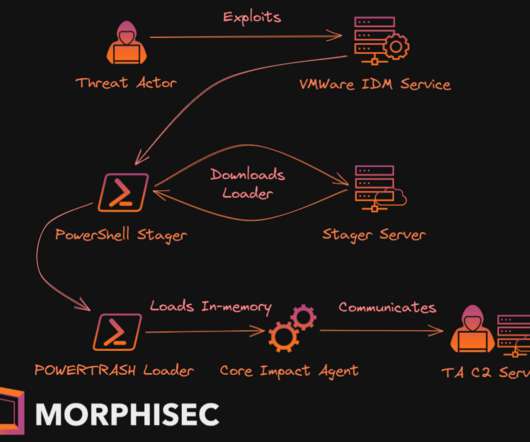


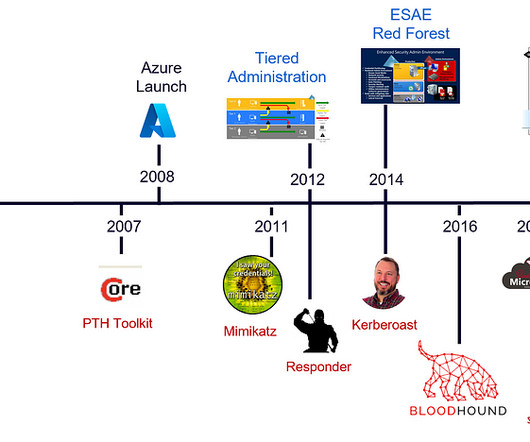







Let's personalize your content