New Mimic Ransomware Uses Windows Search Engine to Find and Encrypt Files
Heimadal Security
JANUARY 30, 2023
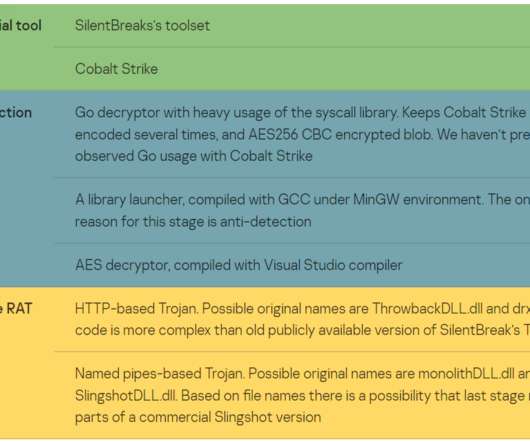
Mimic uses Everything API, a file search tool for Windows, to search for files to encrypt. As a sophisticated malware, […] The post New Mimic Ransomware Uses Windows Search Engine to Find and Encrypt Files appeared first on Heimdal Security Blog.










































Let's personalize your content