Top 10 SOAR Tools to Enhance Your SecOps Experience
Heimadal Security
FEBRUARY 3, 2023
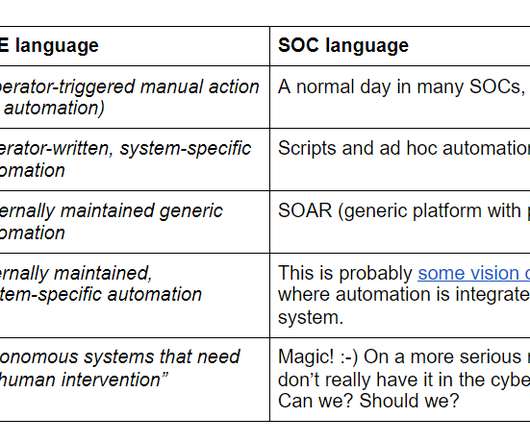
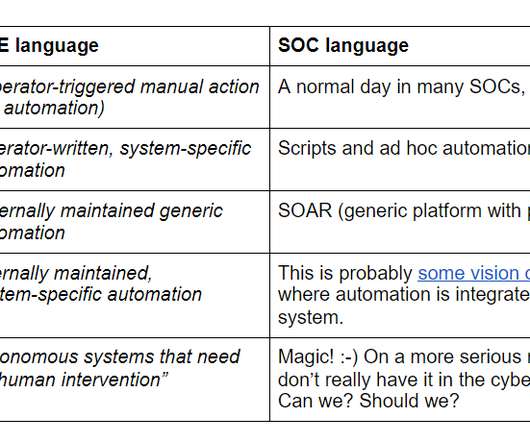
In a previous article, we talked about the core differences (and similarities) between SOAR and XDR. And because no SecOps specialist should be without an adequate toolkit, here are some SOAR tools you can try out to up your security automation game. Good hunting and enjoy the read!









































Let's personalize your content