TrustSec Policy Analytics – Part One: What are policy analytics?
Cisco Security
MAY 24, 2021
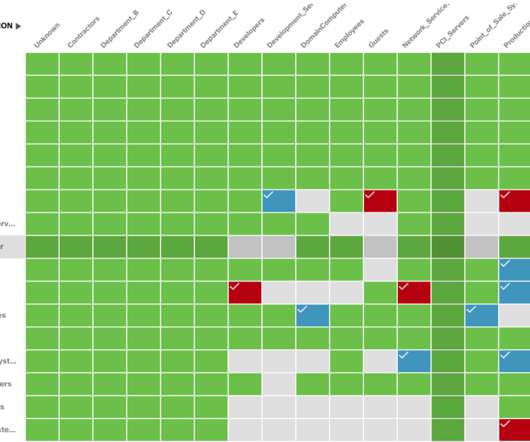
Why all the buzz around pursuing group-based policy management to achieve zero trust? Adopting zero-trust initiatives and best practices is all the rage. Simply put, applying “never trust; always verify” to anyone and any device attempting to access an enterprise network is a no-brainer nowadays. And rightly so.










Let's personalize your content