Change Healthcare data breach impacted over 100 million people
Security Affairs
OCTOBER 25, 2024
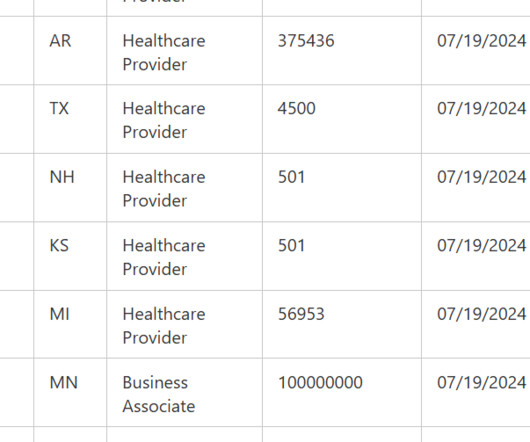
The Change Healthcare data breach in the February 2024 impacted over 100 million, the largest-ever healthcare data breach in the US. UnitedHealth Group announced that the data breach suffered by Change Healthcare in February 2024 impacted more than 100 million individuals.















































Let's personalize your content