Leak of Russian Censorship Data
Schneier on Security
MARCH 14, 2022
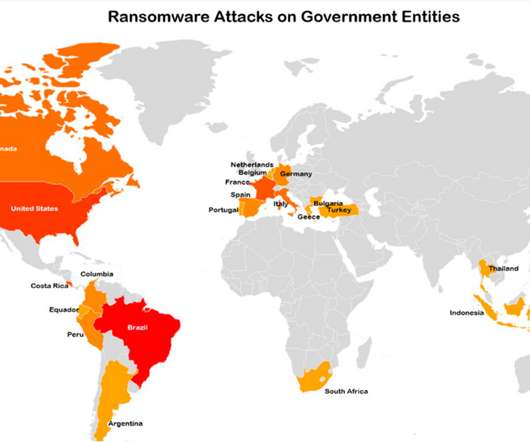
The transparency organization Distributed Denial of Secrets has released 800GB of data from Roskomnadzor, the Russian government censorship organization. Specifically, Distributed Denial of Secrets says the data comes from the Roskomnadzor of the Republic of Bashkortostan.















































Let's personalize your content