Zero Trust Is (also) About Protecting Machine Identities
Security Boulevard
SEPTEMBER 30, 2022
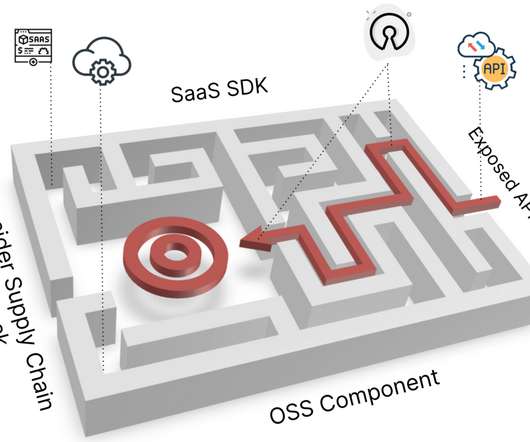
Zero Trust Is (also) About Protecting Machine Identities. Move towards an identity-based Zero Trust cybersecurity approach. The importance of identities is reflected in the recent strategy for a Zero Trust cybersecurity , published by the Office of Management and Budget (OMB).


















































Let's personalize your content