Iranian Agonizing Serpens APT is targeting Israeli entities with destructive cyber attacks
Security Affairs
NOVEMBER 7, 2023
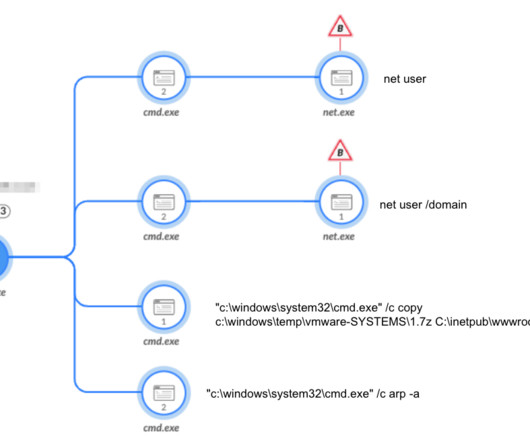
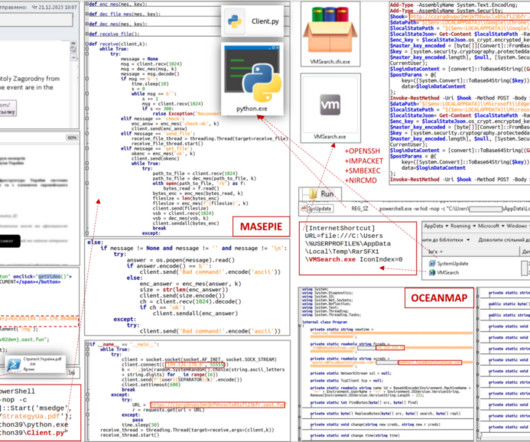
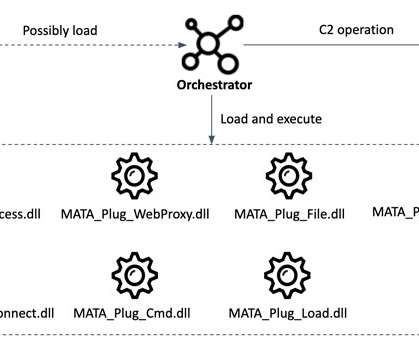
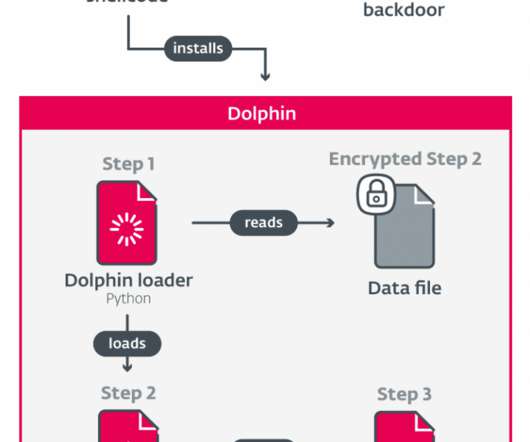
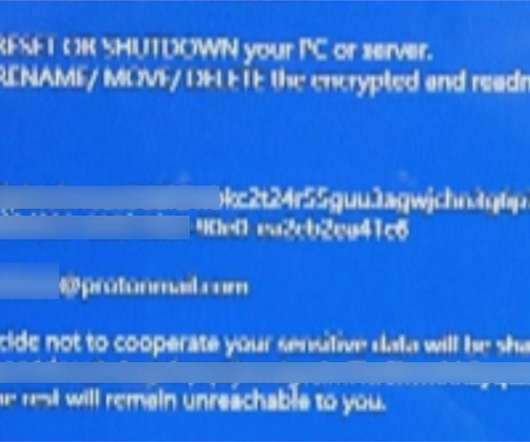
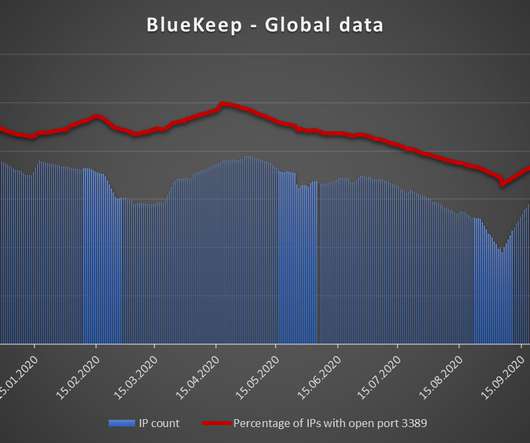
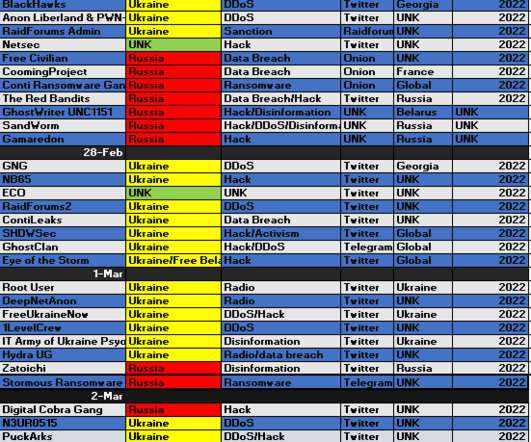
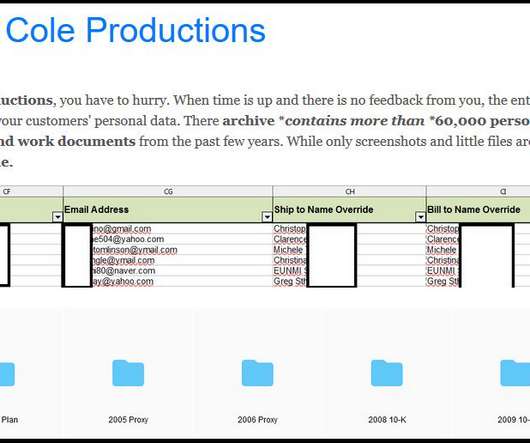
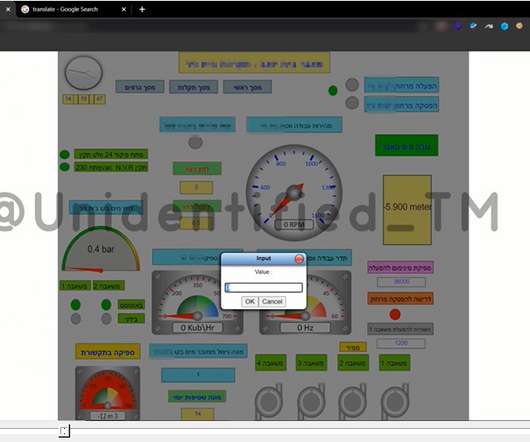
Iran-linked Agonizing Serpens group has been targeting Israeli organizations with destructive cyber attacks since January. personally identifiable information (PII) and intellectual property) and then deploy various wipers to cover the tracks. Then the attackers deployed multiple web shells to gain a foothold in the network.





































Let's personalize your content