Introduction to Fileless Malware
Doctor Chaos
DECEMBER 20, 2022
Fileless malware is a type of cyber attack that does not rely on the traditional method of installing malicious software on a victim's computer.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Doctor Chaos
DECEMBER 20, 2022
Fileless malware is a type of cyber attack that does not rely on the traditional method of installing malicious software on a victim's computer.

Security Affairs
JANUARY 20, 2025
Researchers linked the threat actor DoNot Teamto a new Android malware that was employed in highly targeted cyber attacks. CYFIRMA researchers linked a recently discovered Android malware to the Indian APT group known as DoNot Team. The group persistently employs similar techniques in their Android malware.”
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Jane Frankland
MAY 3, 2025
Allegedly orchestrated by the same group known as Scattered Spider, these attacks highlight the significant challenges even the most respected and established brands face in defending against modern cyber threats. Then, the focus of cyber attacks on retailers, and what lessons must be learned by business leaders and customers.

CyberSecurity Insiders
DECEMBER 3, 2021
All you populace out in UK, please be aware that some online fraudsters are launching phishing email attacks in the name of NHS distributing free PCR testing kits to detect the latest Omicron Corona Virus variant. According to the data privacy group of UK, the phishing campaign is spreading in two email forms.

Hacker's King
MAY 24, 2025
While these octopi of terror could spring from many sources, do you know what the very wellspring of most cyber attacks is? The startling fact is that more than 55% of breaches stem from credential attack vectors. Credential-based attacks include usernames, passwords, and tokens.

CyberSecurity Insiders
FEBRUARY 8, 2022
Microsoft has made it official that it has disabled macros across its office products to block malware cyber attacks. The post Microsoft disables macros to curtail Malware Cyber Attacks appeared first on Cybersecurity Insiders.
Security Affairs
OCTOBER 17, 2024
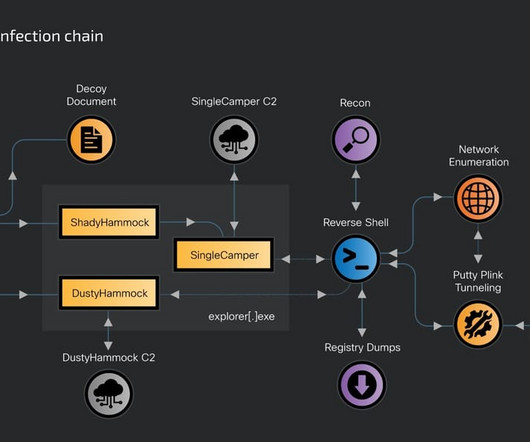
Russia-linked threat actor RomCom targeted Ukrainian government agencies and Polish entities in cyber attacks since late 2023. The group uses multiple tools and malware languages (GoLang, C++, RUST, LUA) to establish long-term access for espionage, possibly followed by ransomware deployment for disruption and profit.

Security Affairs
NOVEMBER 3, 2024
Chinese threat actors use Quad7 botnet in password-spray attacks FBI arrested former Disney World employee for hacking computer menus and mislabeling allergy info Sophos details five years of China-linked threat actors’ activity targeting network devices worldwide PTZOptics cameras zero-days actively exploited in the wild New LightSpy spyware (..)

CyberSecurity Insiders
MARCH 21, 2021
Ways to Protect Your Small Business from Cyber Attacks . . A successful cyber attack can cost you around $3 million! Here are some of the ways to protect your small business from cyber attacks. . A cyber security plan includes the best security practices and protocols for protection. . Firewalls .

Digital Shadows
NOVEMBER 26, 2024
Key Points Phishing incidents rose during the reporting period (August 1 to October 31, 2024), accounting for 46% of all customer incidents. This increase is likely driven by high employee turnover and easy access to phishing kits. Meanwhile, “RansomHub” is rising rapidly due to its attractive ransomware-as-a-service (RaaS) model.

CyberSecurity Insiders
FEBRUARY 19, 2021
The United States Department of Justice has charged 3 North Korean for allegedly launching cyber attacks on many of the banking and cryptocurrency networks operating across the world. attack aka Not Petya ransomware attack. billion in cash and digital currency from entities operating across the world.

Tech Republic Security
JUNE 4, 2024
Organisations providing services related to the Paris Olympics 2024 have an increased risk of cyber attack, a new study has found.
Security Affairs
DECEMBER 29, 2023
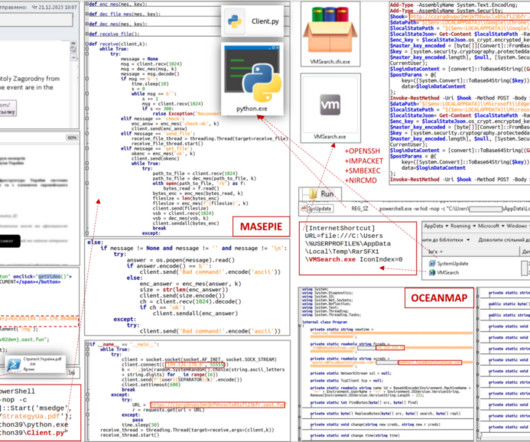
Ukraine’s CERT (CERT-UA) warned of a new phishing campaign by the APT28 group to deploy previously undocumented malware strains. The Computer Emergency Response Team of Ukraine (CERT-UA) warned of a new cyber espionage campaign carried out by the Russia-linked group APT28 (aka “ Forest Blizzard ”, “ Fancybear ” or “ Strontium ”).

CyberSecurity Insiders
MARCH 23, 2021
To all those who are concerned about the increase in cyber attacks on Maritime Industry, here’s an interesting finding to analyze. During a webinar conducted by Riviera, they revealed that the Human errors are causing an increase in cyber attacks on Maritime Industry.
The Hacker News
FEBRUARY 27, 2025
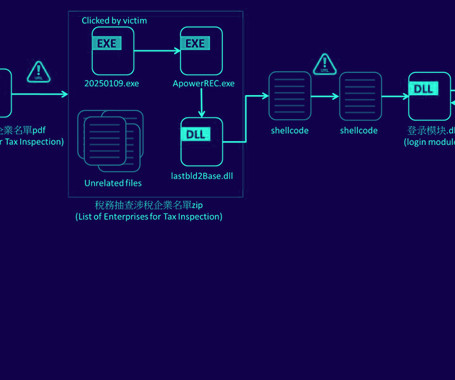
A new campaign is targeting companies in Taiwan with malware known as Winos 4.0 as part of phishing emails masquerading as the country's National Taxation Bureau. The campaign, detected last month by Fortinet FortiGuard Labs, marks a departure from previous attack chains that have leveraged malicious game-related applications.
Security Affairs
NOVEMBER 27, 2021
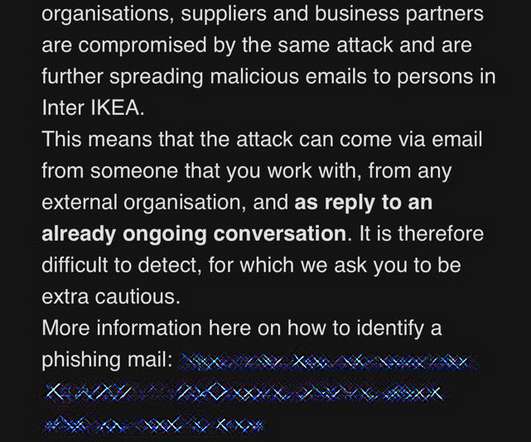
Threat actors are targeting IKEA employees in an internal phishing campaign leveraging stolen reply-chain emails. According to BleepingComputer, threat actors are targeting IKEA employees in phishing attacks using stolen reply-chain emails. “There is an ongoing cyber-attack that is targeting Inter IKEA mailboxes.

Security Affairs
AUGUST 13, 2020
Israel ‘s defence ministry announced to have foiled an attempted cyber attack by a foreign threat actors group targeting the country’s defence manufacturers. According to the officials, the attack was launched by “an international cyber group called ‘ Lazarus.’

CyberSecurity Insiders
JUNE 11, 2021
Electronic Arts confirmed the news and added that no client data or anything related to the players was accessed or stolen by hackers- meaning there are zero risks for players to be targeted with phishing attacks or identity thefts. The post Cyber Attack news trending on Google appeared first on Cybersecurity Insiders.

CyberSecurity Insiders
JANUARY 17, 2022
North Korea, the nation that is being led by Kim Jong UN is back into news headlines for stealing cryptocurrency worth millions through cyber attacks. The post North Korea steals $400m cryptocurrency through Cyber Attacks appeared first on Cybersecurity Insiders.

CyberSecurity Insiders
MAY 7, 2023
It is not accurate to say that 5G networks are completely immune to cyber attacks. Like any other network, 5G networks are vulnerable to various types of cyber attacks, such as distributed denial-of-service (DDoS) attacks, phishing attacks, and malware infections.

SecureWorld News
DECEMBER 4, 2024
The United States retail sector faced an especially aggressive wave of cyber threats, with phishing attacks mimicking major holiday brands [3] including Walmart, Target, and Best Buy increasing by more than 2,000% during peak shopping periods. Also lock down your brand name with official registrations.
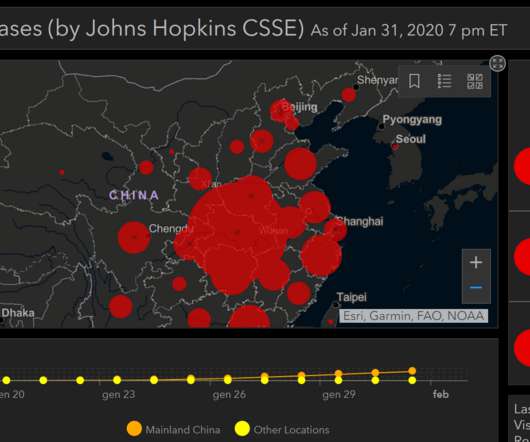
Security Affairs
FEBRUARY 26, 2020
Researchers from Cybaze Yoroi ZLab have spotted a new campaign exploiting the interest in coronavirus (COVID-19) evolution to spread malware. Nowadays, it is common to say that the physical world and the cyber world are strictly connected. The statistics are worrying, and, of course, they represent an opportunity for cyber-crooks.

CyberSecurity Insiders
OCTOBER 24, 2021
A recent statement issued by the Summer Olympics Organizer from Japan revealed that the cyber threat to the games event was so intense that the organizing committee had to hire a third party firm that with a dedicated team of 200 Cybersecurity specialists helped thwart over 500 million or half a billion cyber attacks.

CyberSecurity Insiders
JANUARY 30, 2022
The Work from Home (WfH) culture might do well to the employees, but some companies are disclosing openly that they are witnessing a surge in cyber attacks( mainly data breaches) on their IT infrastructure as their employees are not following basic cyber hygiene of using strong passwords and authenticating their Identity whole accessing networks.

Centraleyes
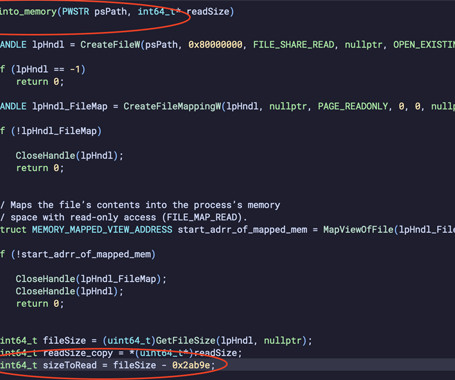
MARCH 20, 2025
By using a dynamic timeline visualization tool, the cybersecurity team pinpointed the entry point and spread trajectory of the malware, halting its progress and restoring operations within hours. Cyber attack data visualization bridges this gap, making technical cyber security data accessible to non-technical audiences.
The Hacker News
JANUARY 20, 2025
Cybersecurity researchers are calling attention to a series of cyber attacks that have targeted Chinese-speaking regions like Hong Kong, Taiwan, and Mainland China with a known malware called ValleyRAT. The infection chain commences with a phishing

Security Affairs
NOVEMBER 20, 2020
According to India Today , experts involved in the investigation have discovered malware at a load dispatch center, which is responsible for ensuring the operation of the power grid, monitoring grid operations, and scheduling and dispatching electricity. ” states India Today. . ” continues the article. Pierluigi Paganini.

CyberSecurity Insiders
SEPTEMBER 12, 2021
All these days, we have seen email phishing attacks where cyber crooks seen sending malicious links through emails to trap online victims. But now, a North Korea-based hacking group dubbed Kumsong 121 was found using social media to attack smart phone users using Android platform.

CyberSecurity Insiders
FEBRUARY 19, 2023
As per the details offered to press, the semiconductor industry that suffered a ransomware attack last year would incur a loss of $250 million in the next quarter. According to the press update provided by the firm, hackers gained access into its server network and installed malware and stole classified information, including source code.

Security Affairs
AUGUST 21, 2024
The Computer Emergency Response Team of Ukraine (CERT-UA) warned of new phishing attacks, carried out by the Vermin group, distributing a malware. The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of a new phishing campaign conducted by the Vermin group that distributed malware.

Security Affairs
DECEMBER 9, 2024
Romanian energy supplier Electrica Group is investigating an ongoing ransomware attack impacting its operations. Romanian energy supplier Electrica Group suffered a cyber attack that is impacting its operations. “Electrica Group is under a cyber attack. The company serves over 3.8 ” reads the note.

Security Affairs
NOVEMBER 10, 2024
Mazda Connect flaws allow to hack some Mazda vehicles Veeam Backup & Replication exploit reused in new Frag ransomware attack Texas oilfield supplier Newpark Resources suffered a ransomware attack Palo Alto Networks warns of potential RCE in PAN-OS management interface iPhones in a law enforcement forensics lab mysteriously rebooted losing their (..)

Schneier on Security
APRIL 7, 2020
From an agency memo : A new wave of cyber-attacks is targeting Federal Agency Personnel, required to telework from home, during the Novel Coronavirus (COVID-19) outbreak. Here are some examples of what's been observed in the past few days: Doubling of email phishing attempts. NASA is reporting an increase in cyberattacks.

Security Affairs
APRIL 11, 2020
Crooks are using a fake Cisco “critical security advisory” in a new phishing campaign aimed at stealing victims’ Webex credentials. The Cofense’s phishing defense center has uncovered an ongoing phishing campaign that uses a Cisco security advisory related to a critical vulnerability as a lure. org/cgi-bin/cvename.cgi?name=CVE-2016-9223.

The Hacker News
DECEMBER 27, 2024
The threat actor known as Cloud Atlas has been observed using a previously undocumented malware called VBCloud as part of its cyber attack campaigns targeting "several dozen users" in 2024.

CyberSecurity Insiders
NOVEMBER 7, 2022
Exploiting zero-day vulnerabilities, phishing, malware attacks, and exploring and exploiting unpatched software issues were being employed by the hacking groups funded by the Xi Jinping led nation. The post China is targeting smaller nations with Cyber Attacks appeared first on Cybersecurity Insiders.

The Hacker News
NOVEMBER 13, 2024
A newly patched security flaw impacting Windows NT LAN Manager (NTLM) was exploited as a zero-day by a suspected Russia-linked actor as part of cyber attacks targeting Ukraine.

Approachable Cyber Threats
MARCH 12, 2025
Category Awareness, Social Enginering Risk Level Phishing emails are getting harder to detect. What is phishing, and why is it such a big deal?" Phishing is one of the oldest tricks in the hacker playbook - but its also one of the most effective. Alright, but cant I just spot and delete phishing emails?"

Webroot
FEBRUARY 21, 2025
Cyber threats are no longer just the occasional virus or suspicious email. Phishing scams, ransomware attacks, data breaches, and identity theft are part of a growing list of online dangers that are a daily reality. Anti-phishing protection Shields you from phishing attempts.

CyberSecurity Insiders
MARCH 10, 2022
Ukraine’s critical infrastructure is being cyber-attacked by malware these days and highly placed sources state that the malicious software has compromised 13 computer networks operating for public utilities so far. The post Ukraine now faces MicroBackdoor malware threat from Russia appeared first on Cybersecurity Insiders.

Security Affairs
MAY 4, 2025
CISA adds SonicWall SMA100 and Apache HTTP Server flaws to its Known Exploited Vulnerabilities catalog Pro-Russia hacktivist group NoName057(16) is targeting Dutch organizations FBI shared a list of phishing domains associated with the LabHost PhaaS platform Canadian electric utility Nova Scotia Power and parent company Emera suffered a cyberattack (..)

Krebs on Security
SEPTEMBER 17, 2020
The government alleges the men used malware-laced phishing emails and “supply chain” attacks to steal data from companies and their customers. Security firm FireEye dubbed that hacking blitz “one of the broadest campaigns by a Chinese cyber espionage actor we have observed in recent years.”
Security Affairs
APRIL 30, 2025
. “The analyses of the TTPs used during APT28 campaigns since 2021 and the recommendations published in October of 2023 remain relevant and may be consulted on the website of the CERT-FR” APT28’s attack chain begins with phishing and brute-force attacks, along with zero-day exploitation (e.g. CVE-2023-23397 ).
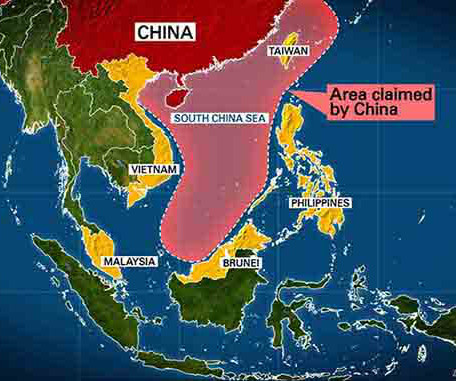
SecureWorld News
MAY 23, 2023
The deepening geopolitical tensions between China and Taiwan have cast a dark shadow over East Asia, triggering a marked rise in cyber attacks on the island nation. A surge in malicious activities According to the Trellix Advanced Research Center , cyber attacks against Taiwan have increased significantly in recent months.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content