Malicious Minecraft mods distributed by the Stargazers DaaS target Minecraft gamers
Security Affairs
JUNE 19, 2025
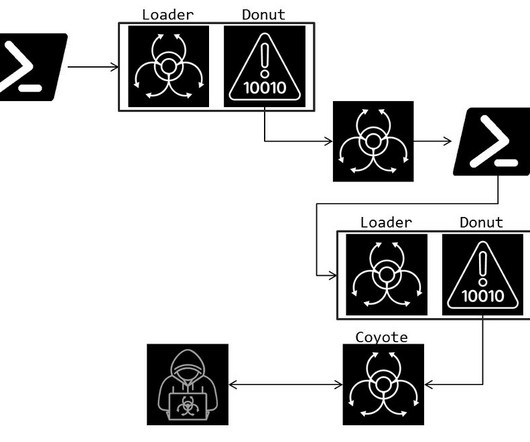
However, this openness has also made it a target for cyber threats. Threat actors employ a multi-stage infection chain, with the first two stages written in Java and requiring the Minecraft runtime to execute, making the threat highly targeted at the game’s user base. ” reads the report published by Check Point.














































Let's personalize your content