What is Cyber Threat Hunting? Definition, Techniques & Steps
eSecurity Planet
FEBRUARY 17, 2023
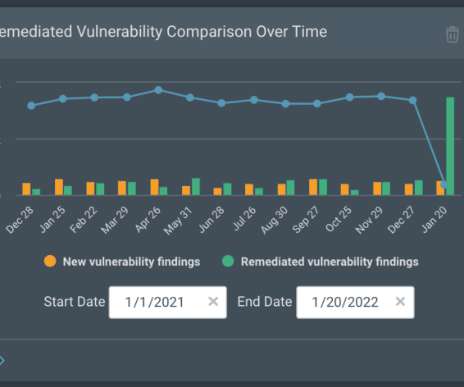
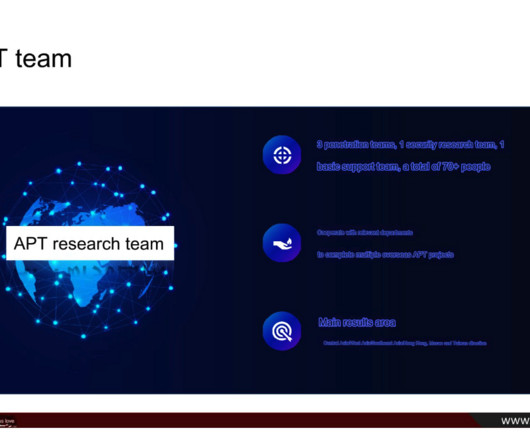
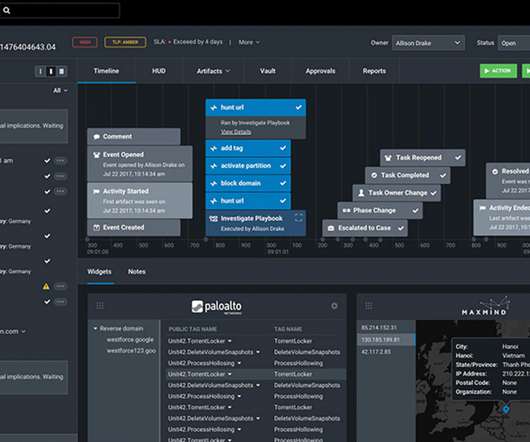
Threat hunting starts with a pretty paranoid premise: That your network may have already been breached and threat actors may be inside waiting for an opportunity to strike. This data is based on common attributes where cyber threat hunters can efficiently identify suspicious activity, making the threat hunting process more manageable.
















































Let's personalize your content