B1txor20 Linux botnet use DNS Tunnel and Log4J exploit
Security Affairs
MARCH 17, 2022
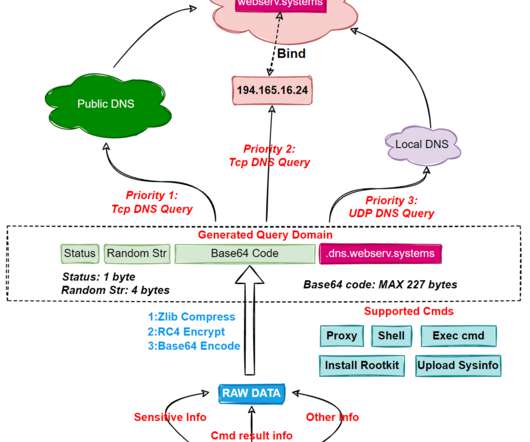
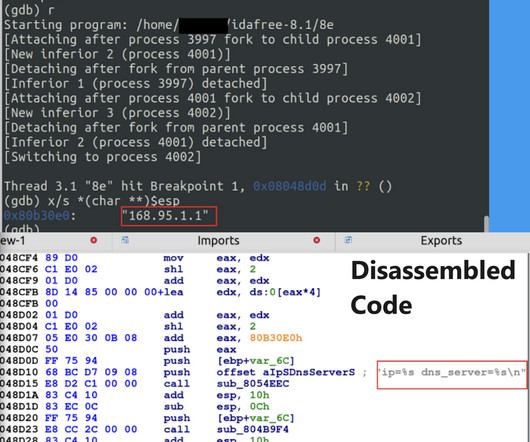
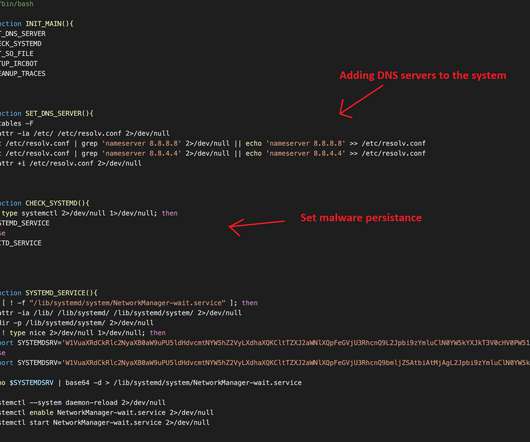
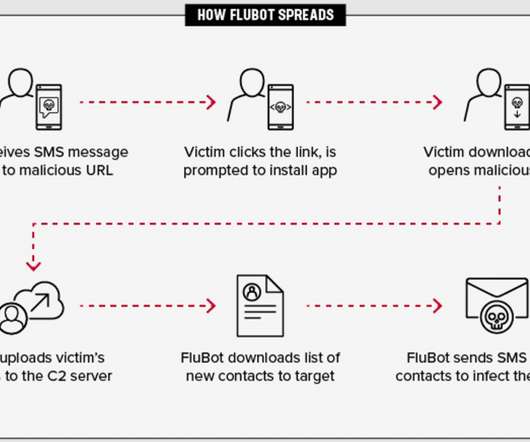
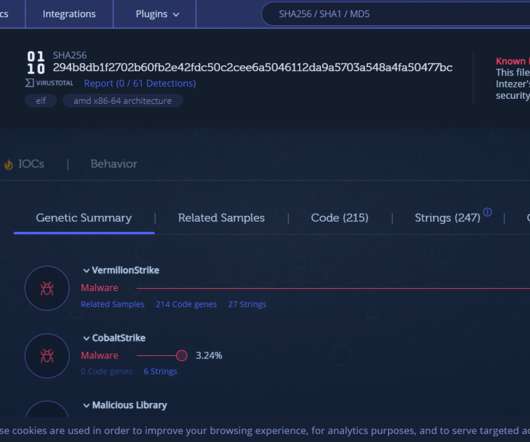
Researchers uncovered a new Linux botnet, tracked as B1txor20, that exploits the Log4J vulnerability and DNS tunnel. “In short, B1txor20 is a Backdoor for the Linux platform, which uses DNS Tunnel technology to build C2 communication channels. In this way, Bot and C2 achieve communication with the help of DNS protocol.”






























Let's personalize your content