Whitepaper: The Intersection of Technical Debt and Cybersecurity
Approachable Cyber Threats
MAY 23, 2022
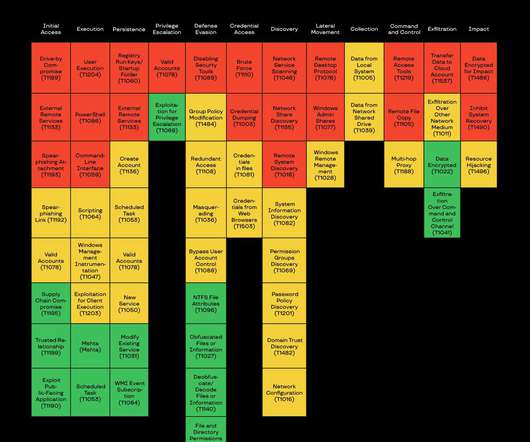
Category Guides, Cybersecurity Fundamentals. Risk Level. With such a wide net, understanding how technical debt impacts your business and cybersecurity efforts can be a challenge. Don’t worry about that documentation for now.” “We We only have one person that knows how to fix this code.” “We DOWNLOAD IT NOW (FREE).












































Let's personalize your content