B1txor20 Linux botnet use DNS Tunnel and Log4J exploit
Security Affairs
MARCH 17, 2022
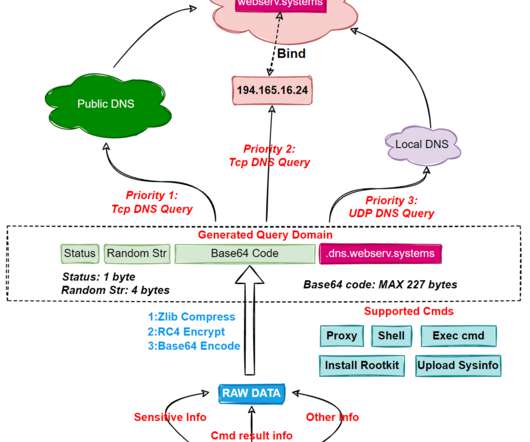
Researchers uncovered a new Linux botnet, tracked as B1txor20, that exploits the Log4J vulnerability and DNS tunnel. The name B1txor20 is based on the file name “b1t” used for the propagation and the XOR encryption algorithm, and the RC4 algorithm key length of 20 bytes. ” reads the analysis published by the experts.







































Let's personalize your content