How can small businesses ensure Cybersecurity?
CyberSecurity Insiders
JUNE 7, 2023
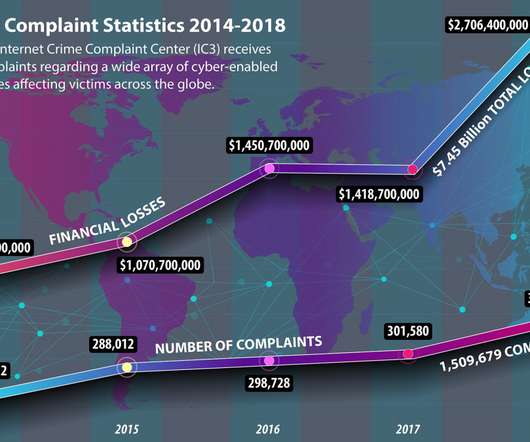
Small businesses are more vulnerable to cyber-attacks since hackers view them as easy victims to target. While this may seem unlikely, statistics reveal that more than half of these businesses experienced some form of cyber-attack in 2022. Therefore, it’s crucial that small businesses make cybersecurity a top priority.














































Let's personalize your content