Roaming Mantis implements new DNS changer in its malicious mobile app in 2022
SecureList
JANUARY 19, 2023
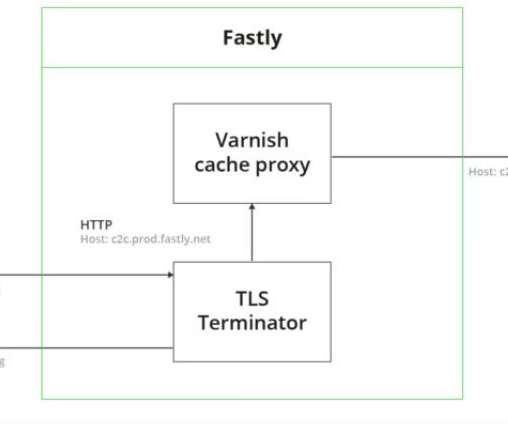
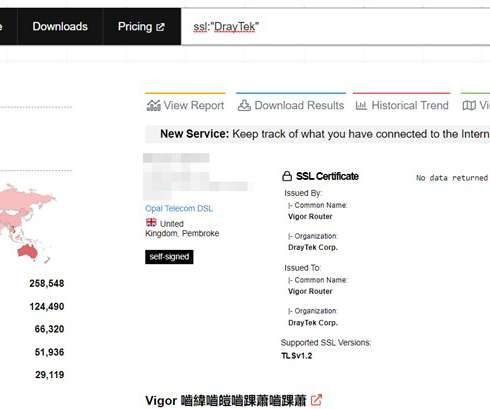
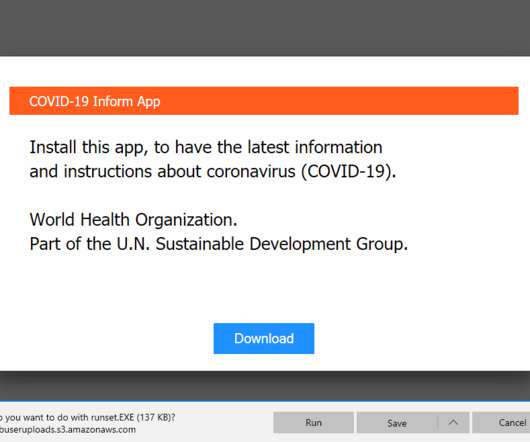
Kaspersky has been investigating the actor’s activity throughout 2022, and we observed a DNS changer function used for getting into Wi-Fi routers and undertaking DNS hijacking. At that time, the criminals compromised Wi-Fi routers for use in DNS hijacking, which is a very effective technique. Agent.eq (a.k.a











































Let's personalize your content