Massive increase in XorDDoS Linux malware in last six months
Malwarebytes
MAY 25, 2022
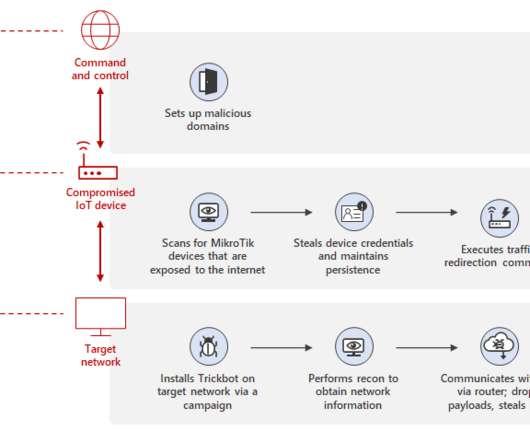
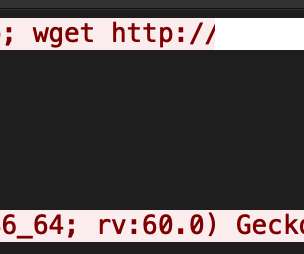
Based on a case study in 2015 , Akamai strengthened the theory that the malware may be of Asian origin based on its targets. Microsoft said that XorDDoS continues to home on Linux-based systems, demonstrating a significant pivot in malware targets. MMD believed the Linux Trojan originated in China.
















































Let's personalize your content