Snake Ransomware isolates infected Systems before encrypting files
Security Affairs
JULY 5, 2020
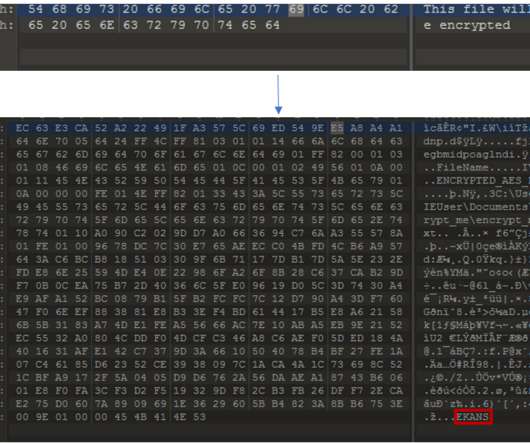
Experts spotted recent samples of the Snake ransomware that were isolating the infected systems while encrypting files to avoid interference. The Snake ransomware kills processes from a predefined list, including ICS-related processes, to encrypt associated files. ” continues the analysis. ” concludes the report.
















































Let's personalize your content