Confucius Uses Pegasus Spyware-related Lures to Target Pakistani Military
Trend Micro
AUGUST 16, 2021
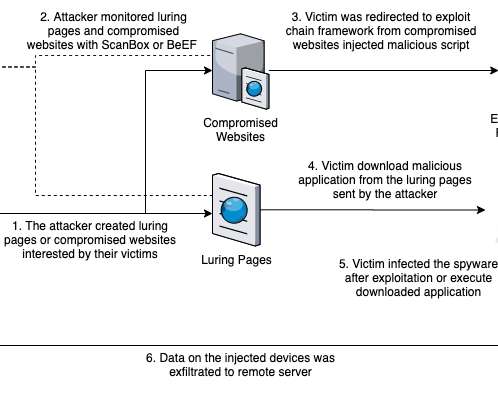
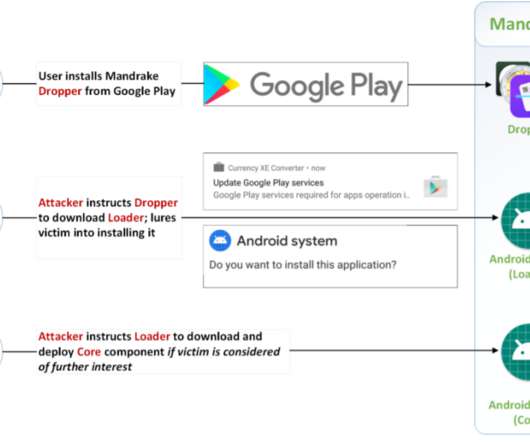
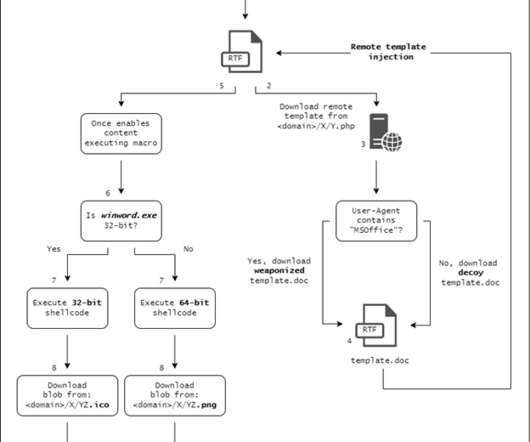
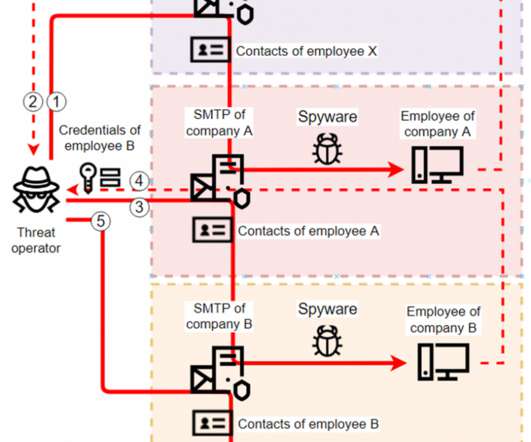
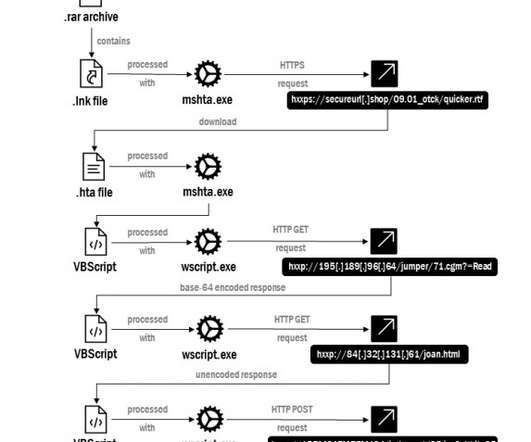
While investigating the Confucius threat actor, we found a recent spear phishing campaign that utilizes Pegasus spyware-related lures to entice victims into opening a malicious document downloading a file stealer.







































Let's personalize your content