Cyberweapons Arms Manufacturer FinFisher Shuts Down
Schneier on Security
APRIL 6, 2022
FinFisher has shut down operations. This is the spyware company whose products were used, among other things, to spy on Turkish and Bahraini political opposition.

Schneier on Security
APRIL 6, 2022
FinFisher has shut down operations. This is the spyware company whose products were used, among other things, to spy on Turkish and Bahraini political opposition.

Krebs on Security
APRIL 6, 2022
Many organizations are already struggling to combat cybersecurity threats from ransomware purveyors and state-sponsored hacking groups, both of which tend to take days or weeks to pivot from an opportunistic malware infection to a full blown data breach. But few organizations have a playbook for responding to the kinds of virtual “smash and grab” attacks we’ve seen recently from LAPSUS$, a juvenile data extortion group whose short-lived, low-tech and remarkably effective tactic
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
APRIL 6, 2022
The Washington Post has revealed details of a contract with a software company that will allow the FBI to track social media posts. The post FBI investing millions in software to monitor social media platforms appeared first on TechRepublic.

Security Boulevard
APRIL 6, 2022
Digital transformation advances all business areas, fundamentally optimizing business processes and delivering value to customers. Successful digital transformation demands speed and agility over a sustained period, necessitating that cybersecurity keeps pace and becomes equally robust and responsive to changes in business and technology. Spending on digital transformation is expected to reach $1.8 trillion in 2022.

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

Tech Republic Security
APRIL 6, 2022
The scam was able to bypass Google and Microsoft’s email security filters after appearing to come from a legitimate email domain. The post Hackers employ voicemail phishing attacks on WhatsApp users appeared first on TechRepublic.

Bleeping Computer
APRIL 6, 2022
American cybersecurity company Palo Alto Networks warned customers on Wednesday that some of its firewall, VPN, and XDR products are vulnerable to a high severity OpenSSL infinite loop bug disclosed three weeks ago [.].
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.
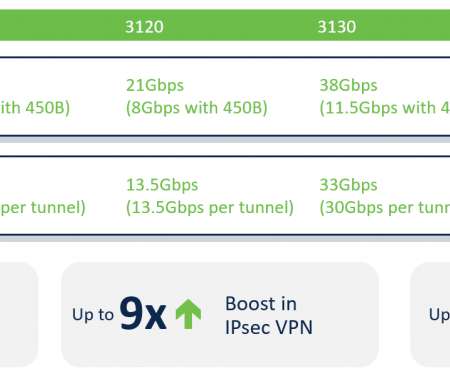
Cisco Security
APRIL 6, 2022
“I so look forward to the next firewall hardware upgrade cycle!”. – No One Ever. Always Give More. If I learned one thing from my firewall customers over the many years, it would be that they like to upgrade their hardware appliances as much as an average consumer likes to shop for a new car. No amount of flashy vendor marketing materials with the obligatory “industry-first” promises peppered all over can make up for this unglamorous exercise.

Tech Republic Security
APRIL 6, 2022
S&P Global Credit adds cybersecurity to list of risk factors for evaluating credit scores and will use NIST standards for the evaluation process. The post Credit agency warns weak cybersecurity defenses could hurt a company’s credit rating, even before an attack appeared first on TechRepublic.

Cisco Security
APRIL 6, 2022
Security has never been more top of mind. Perhaps it’s exacerbated by what’s going on in Ukraine and the challenges it presents to the world, including the real fears over cyberwarfare. Of course, threats becoming advanced, the move to the cloud, and hybrid work remain among our customers’ biggest challenges. Who knew that when we all left the office more than two years ago, we would be gone to for so long—let alone hybrid work and its permanence becoming part of our work-life reality?

We Live Security
APRIL 6, 2022
ESET researchers analyzed three malicious applications targeting customers of eight Malaysian banks. The post Fake e‑shops on the prowl for banking credentials using Android malware appeared first on WeLiveSecurity.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Security Affairs
APRIL 6, 2022
Block disclosed a data breach related to the Cash App investing app and is notifying 8.2 million current and former US customers. The data breach involved a former employee that downloaded some unspecified reports of its Cash App Investing app that contained some U.S. customer information. Cash App is an app that allows users to easily send money, spend money, save money, and buy cryptocurrency. “On April 4, 2022, Block, Inc.
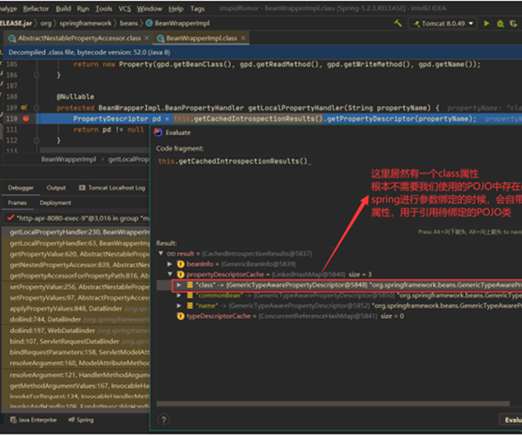
eSecurity Planet
APRIL 6, 2022
Spring4Shell ( CVE-2022-22965 ) is a remote code execution (RCE) vulnerability that affects Spring Core, a comprehensive framework for Java-based enterprise applications. Spring4Shell gets its name from the Log4Shell vulnerability , one of the most critical zero-day threats ever, which affected a Java software component called Log4j and allowed hackers to take control of web servers and networks.

Malwarebytes
APRIL 6, 2022
Unfortunately scammers continue to focus on the invasion of Ukraine to make money. A flurry of bogus domains and scam techniques are spreading their wings. They appear to focus on donation fakeouts but there’s a few other nasty surprises lying in wait too. The lowest of the low. There are few lower tactics than fake fundraising during times of crisis.

Security Affairs
APRIL 6, 2022
Ukraine’s technical security and intelligence service warns of threat actors targeting aimed at gaining access to users’ Telegram accounts. State Service of Special Communication and Information Protection (SSSCIP) of Ukraine spotted a new wave of cyber attacks aimed at gaining access to users’ Telegram accounts. The Ukrainian CERT attributes the hacking campaign to threat actors tracked as UAC-0094.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Hacker Combat
APRIL 6, 2022
Ransomware attacks targeting governments, businesses, hospitals, and private individuals are rising. It has become a vast online issue that affects individuals and businesses alike. You are neither safe on your private nor public network, as ransomware can encrypt your files and hold them hostage. As a result, you have to pay ransom to unlock them. With so many businesses affected, there needs to be some way to combat this attack.

Security Affairs
APRIL 6, 2022
The U.S. Treasury Department sanctioned the Hydra Market, the world’s largest and longest-running dark web marketplace. The U.S. Treasury Department sanctioned the darkweb marketplace Hydra Market, the same day Germany’s Federal Criminal Police Office, the Bundeskriminalamt (BKA), announced they have shut down the illegal platform. The seizure of the Hydra Market is the result of an international investigation conducted by the Central Office for Combating Cybercrime (ZIT) in partnership wi

Identity IQ
APRIL 6, 2022
Common Tech Support Scams and How to Avoid Them. IdentityIQ. These days, we live our lives online. Whether we’re ordering groceries or looking for new shoes, all we need to do is create an account, fill out some basic personal details and log in. But what happens when that account is compromised – or when we think that account is compromised? Maybe you get an email from technical support letting you know that your account has been breached and steps are needed to make it secure again.

Security Affairs
APRIL 6, 2022
Nordex Group, one of the largest manufacturers of wind turbines, was hit by a cyberattack that forced the company to shut down part of its infrastructure. Nordex Group, one of the world’s largest manufacturers of wind turbines, was the victim of a cyberattack that forced the company to take down multiple systems. The attack was uncovered on March 31 and the company immediately started its incident response procedure to contain the attack.

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.

Naked Security
APRIL 6, 2022
Why are Tor sites hard to locate and therefore difficult to take down? We explain in plain English.

CSO Magazine
APRIL 6, 2022
Since its inception in 2020, Zoom’s private bug bounty program has awarded $2.4 million in payments and swag to security researchers, recruiting over 800 ethical hackers via the HackerOne platform. In 2021 alone, it paid $1.8 million to researchers for helping to identify and resolve more than 400 security bugs, with its bounties now ranging from $250 up to $50,000.

Graham Cluley
APRIL 6, 2022
Graham Cluley Security News is sponsored this week by the folks at Axonius. Thanks to the great team there for their support! From new device types to the shift to hybrid work, the introduction of cloud infrastructure, and the rapid increase in SaaS adoption, complexity is increasing rapidly in IT and security environments. And what … Continue reading "Control IT and SaaS complexity with Axonius".

Threatpost
APRIL 6, 2022
Threat actors target Office 365 and Google Workspace in a new campaign, which uses a legitimate domain associated with a road-safety center in Moscow to send messages.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Bleeping Computer
APRIL 6, 2022
An ongoing outage affects numerous Atlassian customers, causing their Jira and Confluence instances to not be accessible for over twenty-four hours. [.].

Heimadal Security
APRIL 6, 2022
A lasting malicious campaign employed by threat actors linked to the Chinese government has been recently discovered by security experts. Its purpose is the launching of a custom malware loader by means of the VLC Media Player. A Chinese state-backed advanced persistent threat (APT) group is attacking organizations around the globe in a likely espionage […].

CyberSecurity Insiders
APRIL 6, 2022
All Apple iPhone and iPAD users are issued a warning about a critical zero day vulnerability that has to be fixed on an immediate note. The technology company has issued a fix to the vulnerability that not only quashes the flaw but also protects device users from poor battery life. So, it is better if all iPhone and iPAD users navigate to the General tab> software updates and download and install the latest version of operating system, i.e. iOS 15.4.1.

SecureBlitz
APRIL 6, 2022
What are the SimpliSafe packages? Read this post to find out… SimpliSafe is one of the most well-known brands in home security. They offer a variety of packages that meet all your needs. To help you decide which package is best for you, this blog post provides information on both their various plans and what’s. The post What Are The SimpliSafe Packages?

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Heimadal Security
APRIL 6, 2022
Developed by Block, Inc., Cash App is a mobile payment service that enables customers to send money to one another using a mobile phone application. Currently, the service is only accessible in two countries: the United Kingdom and the United States. What Happened? Cash App is alerting 8.2 million current and past clients in the […]. The post CashApp Customers Affected by Data Breach appeared first on Heimdal Security Blog.

SecureBlitz
APRIL 6, 2022
In this post, we will show you the SimpliSafe review Reddit users disclosed. Keeping our home secure from intruders is essential when you just moved to a new house or you want to upgrade your old house security from environmental threats. It is not bad to think of securing our home and SimpliSafe is here. The post SimpliSafe Review By Reddit Users appeared first on SecureBlitz Cybersecurity.

Bleeping Computer
APRIL 6, 2022
Microsoft has reminded customers that multiple.NET Framework versions signed using the insecure Secure Hash Algorithm 1 (SHA-1) will reach their end of life this month. [.].

SecureBlitz
APRIL 6, 2022
Can SimpliSafe be hacked? Find out our honest answer in this post. As there is nothing more important than securing or monitoring your home while you are at work or home. SimpliSafe is a popular and one of the first no-contract DIY smart security systems for home. And when you decide to use SimpliSafe for. The post Can SimpliSafe Be Hacked? [Honest ANSWER] appeared first on SecureBlitz Cybersecurity.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Let's personalize your content