The 10 worst tech stories of 2021
Tech Republic Security
DECEMBER 27, 2021
Have fond memories of 2021? They probably don't include these 10 stories or the products and services surrounding them.

Tech Republic Security
DECEMBER 27, 2021
Have fond memories of 2021? They probably don't include these 10 stories or the products and services surrounding them.

CyberSecurity Insiders
DECEMBER 27, 2021
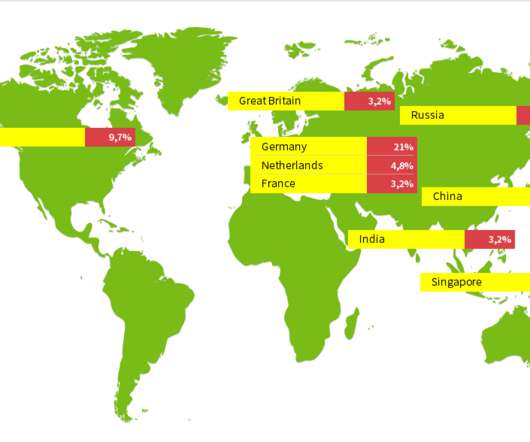
Google, the American web search giant, was technically penalized $100m by Russian government for failing to adhere to its state prevailing laws. Sources state that the Putin led government decided to impose a hefty fine on Google, as it failed to remove the content that was deemed to be inappropriate to Russian web service seekers. Thus, the announced penalty is the largest fine ever slapped by a Russian court in the history and will represent over 6.7% revenue earned by the internet juggernaut
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
DECEMBER 27, 2021
Dark data is a major challenge in enterprises, and it's not going away soon. Fortunately, there are ways to reduce dark data and the risks that come with it.

Security Boulevard
DECEMBER 27, 2021
Let’s take a Cyber Drink to 2021 Cybersecurity professionals have been put in the spotlight this year. We applaud your hard work and service to protect society as the threats only get more sophisticated and the consequences become more frightening. Gone are the days when cybersecurity could operate in a silo. It’s now a business. Read article > The post A Toast to the Cybersecurity Incidents of 2021 appeared first on Axio.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Tech Republic Security
DECEMBER 27, 2021
Many employers are now offering digital security benefits to help protect their employees. Learn about such arrangements and see how you can get started implementing them.

Bleeping Computer
DECEMBER 27, 2021
Users of QNAP network-attached storage (NAS) devices are reporting attacks on their systems with the eCh0raix ransomware, also known as QNAPCrypt. [.].
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.
Security Affairs
DECEMBER 27, 2021
Researchers from DrWeb monitored attacks leveraging exploits for vulnerabilities in the Apache Log4j library. Researchers from DrWeb monitored attacks leveraging exploits for vulnerabilities (CVE-2021-44228, CVE-2021-45046, CVE2021-4104, and CVE-2021-42550) in the Apache Log4j library warning of the need to adopt protective measures. The vulnerabilities can allow threat actors to execute arbitrary code on the target systems, trigger a Denial of Service condition, or disclose confidential informa

CyberSecurity Insiders
DECEMBER 27, 2021
As 2021 draws to a close, it provides an opportunity to reflect on the past year, and the success and growth we have achieved together. Under the backdrop of escalating cyber threats and a continuing global pandemic, (ISC)² members have demonstrated to the world that remote work can be effective and drive enhanced collaboration and innovation. Together we stood up for diversity, equity and inclusion as a critical way to close the workforce gap and continued our commitment to refining and growing

We Live Security
DECEMBER 27, 2021
As we close out another year like no other, let's look back at some of the most notable cybersecurity stories that shaped 2021. The post 2021 in review: The biggest cybersecurity stories of the year appeared first on WeLiveSecurity.
Security Affairs
DECEMBER 27, 2021
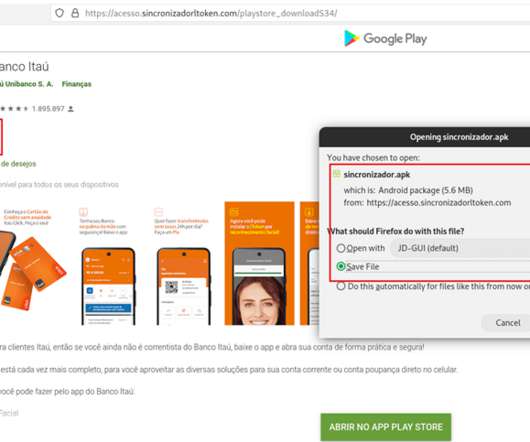
Researchers analyzed a new Android banking malware that targets Brazil’s Itaú Unibanco that spreads through fake Google Play Store pages. Researchers from threat intelligence firm Cyble analyzed a new Android banking malware that targets Brazil’s Itaú Unibanco trying to perform fraudulent financial transactions on the legitimate Itaú Unibanco applications without the victim’s knowledge.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

CyberSecurity Insiders
DECEMBER 27, 2021
If you are in thinking that your PC or computing device is secure enough as it is loaded with an anti-malware solution, you better change your viewpoint. As some hackers have developed a malware that uses code signing certificates to avoid detection by security defenses and has the tendency to download payloads onto a compromised system. Dubbed as ‘Blister’ malware and discovered by researchers from Elastic Security, the malware seems to evade most of the known security defenses and also has the

InfoWorld on Security
DECEMBER 27, 2021
Earlier this month, security researchers uncovered a series of major vulnerabilities in the Log4j Java software that is used in tens of thousands of web applications. The code is widely used across consumer and enterprise systems, in everything from Minecraft, Steam, and iCloud to Fortinet and Red Hat systems. One analyst estimate millions of endpoints could be at risk.

Security Affairs
DECEMBER 27, 2021
A new wave of ech0raix ransomware attacks is targeting QNAP network-attached storage (NAS) devices. The threat actors behind the ech0raix ransomware are targeting NAP network-attached storage (NAS) devices. Users reported numerous compromises of their devices a few days before Christmas. According to BleepingComputer , forum users reported an intensification of the attacks since December 20, the analysis of submissions to the ID ransomware service for this specific threat started to increase on
The State of Security
DECEMBER 27, 2021
This blog contains a discussion about stress, trauma, and domestic violence. This may be difficult for some readers, and given the alarming figures around Post-Traumatic Stress Disorder (PTSD), trauma, and early life experiences (ACEs), this will likely concern at least a small population of readers. Please take care of yourself when reading this and break […]… Read More.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Security Boulevard
DECEMBER 27, 2021
In 2021, we’ve witnessed cybercriminals infiltrate government networks, incessant ransomware lockdown operational technology, and advanced persistent threats make national headlines. Microsoft’s President Brad Smith recently stated, “So there’s been an ongoing conversation in the cybersecurity community. ‘Why aren’t organizations doing…. The post The Future of Government Cybersecurity appeared first on LogRhythm.

Bleeping Computer
DECEMBER 27, 2021
Microsoft has confirmed a new issue impacting devices running Windows 11, version 21H2, where apps using Win32 APIs to render colors on some high dynamic range (HDR) displays may not work as expected. [.].
Security Boulevard
DECEMBER 27, 2021
A nod to military bike history can be found in a new article about the British military called “Charge of the light brigade: Army Parachute Regiment trial electric bikes” Eighty years ago, wartime necessitated the introduction of the Royal Enfield WD/RE ‘Flying Flea’ and the Welbike, which were parachuted into occupied Europe, providing a means … Continue reading Armies Around the World Testing Electric Bikes (Yet Again) ?.

The Hacker News
DECEMBER 27, 2021
Peter Parker might not be a mastermind cryptocurrency criminal, but the name Spiderman is quickly becoming more associated with the mining landscape. ReasonLabs, a leading provider of cybersecurity prevention and detection software, recently discovered a new form of malware hacking into customer computers in the guise of the latest Spiderman movie.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Security Boulevard
DECEMBER 27, 2021
Smart home systems are revolutionizing entertainment and convenience. They also contain loads of personal information that make them popular targets for cybercriminals. However, those who understand smart home security threats and the risks associated with them can plan accordingly. Then, these individuals can ensure their smart home devices are properly protected. 5 Smart Home Security [.].

The Hacker News
DECEMBER 27, 2021
A number of security flaws have been uncovered in a networking component in Garrett Metal Detectors that could allow remote attackers to bypass authentication requirements, tamper with metal detector configurations, and even execute arbitrary code on the devices.

CyberSecurity Insiders
DECEMBER 27, 2021
The post Learn to Lead with Cybersecurity and Defeat Modern Adversaries appeared first on Fidelis Cybersecurity. The post Learn to Lead with Cybersecurity and Defeat Modern Adversaries appeared first on Cybersecurity Insiders.

Acunetix
DECEMBER 27, 2021
As 2021 comes to an end, it is time to sum up the year to see what it meant for Acunetix, Invicti, and the web application security industry. The rise of Invicti 2021 was the year when Acunetix became a brand of Invicti Security. The. Read more. The post 2021 – the year in review appeared first on Acunetix.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

The Hacker News
DECEMBER 27, 2021
Cybercrime is increasing exponentially and presents devastating risks for most organizations. According to Cybercrime Magazine, global cybercrime damage is predicted to hit $10.5 trillion annually as of 2025. One of the more recent and increasingly popular forms of tackling such issues by identifying is ethical hacking.

Acunetix
DECEMBER 27, 2021
As 2021 comes to an end, it is time to sum up the year to see what it meant for Acunetix, Invicti, and the web application security industry. The rise of Invicti 2021 was the year when Acunetix became a brand of Invicti Security. The. Read more. The post 2021 – the year in review appeared first on Acunetix.

Security Boulevard
DECEMBER 27, 2021
e at MixMode have accomplished a lot in 2021. As we approach the end of December we thought it would be a good opportunity to take a look back at the year and highlight the stories and news that we believe exemplify our forward momentum in what continues to be a challenging year for all. The post 2021 Highlights: Pushing Through a Pandemic to Deliver Cybersecurity Innovation with Third-Wave AI appeared first on Security Boulevard.

Dark Reading
DECEMBER 27, 2021
To protect their staffers, leaders should focus on identifying and alleviating root causes of burnout.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Security Affairs
DECEMBER 27, 2021
A researcher found a dozen vulnerabilities in mySCADA myPRO product, some of which have been rated as critical. mySCADA myPRO is a multiplatform, human-machine interface (HMI) and supervisory control and data acquisition (SCADA) system that allows to visualize and control industrial processes. The security researcher Michael Heinzl discovered multiple vulnerabilities in the myPRO product, some of which have been rated as critical severity.

Security Boulevard
DECEMBER 27, 2021
In 2021, we endured the fallout of a seemingly endless parade of privacy controversies and milestone cyber attacks. Related: The dire need to security-proof APIs. The Solar Winds hack demonstrated supply chain exposures; the attempted poisoning of a Tampa suburb’s … (more…). The post ROUNDTABLE: What happened in privacy and cybersecurity in 2021 — and what’s coming in 2022 appeared first on Security Boulevard.

Security Affairs
DECEMBER 27, 2021
The operators of the ToRReZ dark web marketplace have shut down their operation claiming it is the result of their own’s decision. The operators of the ToRReZ dark web marketplace have shut down their operation before Christmas, claiming that it is the result of their own’s decision. The admin of Torrez market “ mrblonde ” made the announcement of the closure of the marketplace on a hacking forum.

Security Boulevard
DECEMBER 27, 2021
What a difference an ‘s’ makes. This seemingly unimportant change could have a big—if unseen—impact. The post Best of 2021 – Chrome to Enforce HTTPS Web Protocol (Like It or Not) appeared first on Security Boulevard.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content