Is Your Government Organization Cyber Resilient?
Lohrman on Security
AUGUST 7, 2022
What does it mean to be prepared for technology and business disruptions in the 2020s? How can your organization recover fast?
Lohrman on Security
AUGUST 7, 2022
What does it mean to be prepared for technology and business disruptions in the 2020s? How can your organization recover fast?

Daniel Miessler
AUGUST 7, 2022
A number of security people have come out against Amazon buying One Medical. It’s to be expected, as most security people are rightly worried about big corporations getting a hold of more personal data. And the timing couldn’t have been worse, with the story about Amazon sharing Ring footage with police only a few weeks old. "Why is @Amazon acquiring @OneMedical bad news?
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
AUGUST 7, 2022
A massive cyberattack hit the website of the German Chambers of Industry and Commerce (DIHK) this week. A massive attack hit the website of the German Chambers of Industry and Commerce (DIHK) forcing the organization to shut down its IT systems as a precautionary measure for security reasons. Aktuell wird intensiv an Lösung und Abwehr gearbeitet. Wir informieren Sie hier, welche Anwendungen wieder funktionsfähig sind: [link] #IHK #DIHK pic.twitter.com/5OHMOLH7Mz — DIHK (@DIHK_News) August

The State of Security
AUGUST 7, 2022
Life among America’s nearly 32 million small businesses has never been easy. According to the Small Business Administration, about 20% of small business startups fail in their first year and half succumb to failure within five years. Bigger businesses have always had more capital, better access to loans, and more staying power. Lately, survival has […]… Read More.

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

Security Affairs
AUGUST 7, 2022
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs free for you in your email box. If you want to also receive for free the newsletter with the international press subscribe here. Greek intelligence service used surveillance malware to spy on a journalist, Reuters reports Slack resets passwords for about 0.5% of its users due to the exposure of salted password hashes Twitter confirms zero-day used to access data of 5.4 millio

Appknox
AUGUST 7, 2022
Penetration Testing has become indispensable to most companies' secure software development lifecycle. Unfortunately, because of widespread misconceptions, several businesses still don't understand the true potential of pen testing and refrain from using it to ensure mobile app security. However, this article will clear those myths and help you with a reality check on penetration testing for mobile applications.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Malwarebytes
AUGUST 7, 2022
Cisco has released a security advisory about several vulnerabilities in the Cisco Small Business RV series routers, covering the RV160, RV260, RV340, and RV345. There are no workarounds available that address these vulnerabilities, so you need to patch. Vulnerabilities. The vulnerabilities are dependent on one another—exploitation of one of the vulnerabilities may be required to exploit another vulnerability.

CyberSecurity Insiders
AUGUST 7, 2022
Research carried out by Reversing Labs suggests that a new ransomware is invading government related Linux Systems in South Korea and the malware is mainly targeting industries and pharmaceutical companies. Cybersecurity researchers from Reversing Labs suggest the ransomware name is GwisinLocker and is probably being developed and distributed by a state funded group of North Korea.
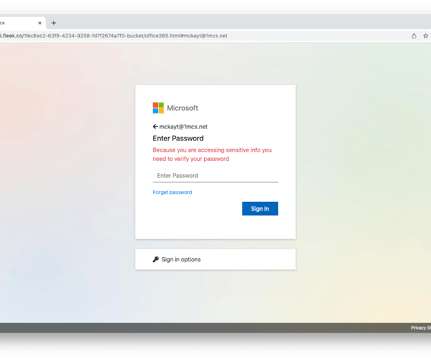
Security Affairs
AUGUST 7, 2022
Threat actors abuse open redirects on Snapchat and American Express to launch phishing attacks against Microsoft 365 users. Attackers abused open redirects on the websites of Snapchat and American Express as part of a phishing campaign targeting Microsoft 365 users. The term Open URL redirection, open redirects, refers to a security issue that makes it easier for attackers to direct users to malicious resources under the control of the attackers.

Malwarebytes
AUGUST 7, 2022
Gas and electricity price concerns are rife at the moment, with spiralling costs and bigger increases waiting down the line. Sadly this makes the subject valuable material for fraudsters, playing into people’s fears with a dash of social engineering to make them worse off than they were previously. Warnings abound of several energy / cost of living-themed scams doing the rounds.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Bleeping Computer
AUGUST 7, 2022
A new social engineering campaign by the notorious North Korean Lazarus hacking group has been discovered, with the hackers impersonating Coinbase to target employees in the fintech industry. [.].

CyberSecurity Insiders
AUGUST 7, 2022
A sophisticated cyber attack has reportedly disrupted the services of NHS UK’s telephone based medical service 111 number severely delaying response to medical emergencies. The downtime was caused because of a software glitch on the servers of Advanced, a privately owned software company that supplies technical services to the medical hotline service.

Bleeping Computer
AUGUST 7, 2022
Attackers abused open redirects on the websites of Snapchat and American Express in a series of phishing attacks to steal Microsoft 365 credentials. [.].

Trend Micro
AUGUST 7, 2022
Understand the cybersecurity risks in the Metaverse.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Security Affairs
AUGUST 7, 2022
Microsoft is actively blocking Tutanota email addresses from registering a Microsoft Teams account. Tutanota is an end-to-end encrypted email app and a freemium secure email service, as of March 2017, Tutanota’s owners claimed to have over 2 million users. The news is that Microsoft is actively blocking Tutanota email addresses from registering a Microsoft Teams account. “Politicians on both sides of the Atlantic are discussing stronger antitrust legislation to regulate Big Tech R

Trend Micro
AUGUST 7, 2022
With geopolitical tensions running high, oil and gas companies may be more susceptible to cyberattacks.

WIRED Threat Level
AUGUST 7, 2022
Whether you want to turn off link previews or block unwanted FaceTime calls, here's what you need to know.

Security Boulevard
AUGUST 7, 2022
What does it mean to be prepared for technology and business disruptions in the 2020s? How can your organization recover fast? The post Is Your Government Organization Cyber Resilient? appeared first on Security Boulevard.

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.
Malwarebytes
AUGUST 7, 2022
Last week on Malwarebytes Labs: Have we lost the fight for data privacy? Lock and Code S03E16. Wrestling star Mick Foley’s Twitter compromised, selling PS5 consoles. Millions of Arris routers are vulnerable to path traversal attacks. When a sextortion victim fights back. How to protect yourself and your kids against device theft. For months, JusTalk messages were accessible to everyone on the Internet.
Security Boulevard
AUGUST 7, 2022
Security Risk by Accepting Policy Exceptions. When an exception to the rule becomes a security breach. I was profoundly shocked after reading the cybersecurity act of 2021. The action called for a 120-day study by the CISA on the various attack vectors impacting the K-12 school districts. Additional mandates include recommendations to deal with malware and ransomware.

Notice Bored
AUGUST 7, 2022
when threat exploits vulnerability causing impact. tough to measure, express and control. the product of probability and impact. the gap between theory and practice. the root of pessimism and optimism. the once-in-a-hundred-years event. needing seatbelt s and airbags. a hair's breadth from disaster. the possibility of exploitation. mitigated but not eliminated. a factor to be borne in mind. inevitable in the Real World. what keeps us up at night. not going entirely to plan. outcome =/= predictio

Security Boulevard
AUGUST 7, 2022
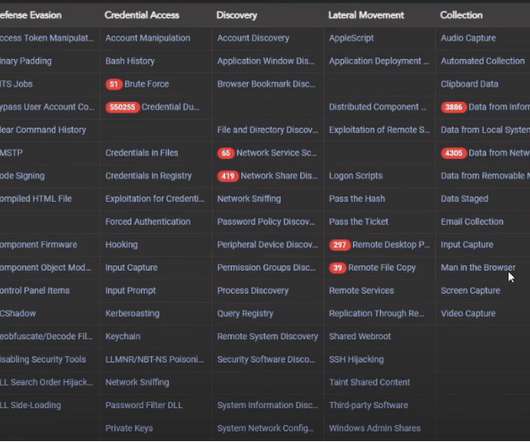
Threat Synopsis – Red Team Tools Over the years Threat Actors have steadily adopted the use of red team tools (sometimes referred to as offensive security tools), most notably Cobalt Strike. These tools have tremendous power, utility and are steadily updated with new capabilities and techniques to evade detection or perform actions in a compromised […].

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Security Boulevard
AUGUST 7, 2022
via the comic artistry and dry wit of Randall Munroe , resident at XKCD ! Permalink. The post XKCD ‘Asking Scientists Questions’ appeared first on Security Boulevard.

Security Boulevard
AUGUST 7, 2022
Richard Moore, Chief of MI6, UK Secret Intelligence Service. Moderator: Jim Sciutto, Chief National Security Correspondent, CNN. Our thanks to The Aspen Institute for publishing their cogent conference videos on the organization's YouTube channel. Permalink. The post Aspen Security Forum 2022 – Moderator: Jim Sciutto – Fireside Chat With Richard Moore appeared first on Security Boulevard.

Security Boulevard
AUGUST 7, 2022
Life among America’s nearly 32 million small businesses has never been easy. According to the Small Business Administration, about 20% of small business startups fail in their first year and half succumb to failure within five years. Bigger businesses have always had more capital, better access to loans, and more staying power. Lately, survival has […]… Read More.

Security Boulevard
AUGUST 7, 2022
Why your phone number is becoming a popular way to identify you, our advise on how to best protect your privacy at hacker summer camp in Las Vegas (BSides, BlackHat, DEF CON), and details on Samsung’s new repair mode which will protect your private data on your smartphone when you take it in for repairs. […]. The post Phone Numbers Used for Identification, Hacker Summer Camp Advice, Samsung Repair Mode appeared first on The Shared Security Show.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Security Boulevard
AUGUST 7, 2022
Kay Bailey Hutchison, Former U.S. Permanent Representative to NATO. Representative Brendan Boyle, Member, House Committee on Ways and Means. Ivo Daalder, Former U.S. Permanent Representative to NATO. Marcin Przydacz, Deputy Foreign Minister, Poland. Moderator: Dafna Linzer, Executive Editor, POLITICO. Our thanks to The Aspen Institute for publishing their cogent conference videos on the organization's YouTube channel.
Let's personalize your content