Operation Triangulation: Zero-Click iPhone Malware
Schneier on Security
JUNE 9, 2023
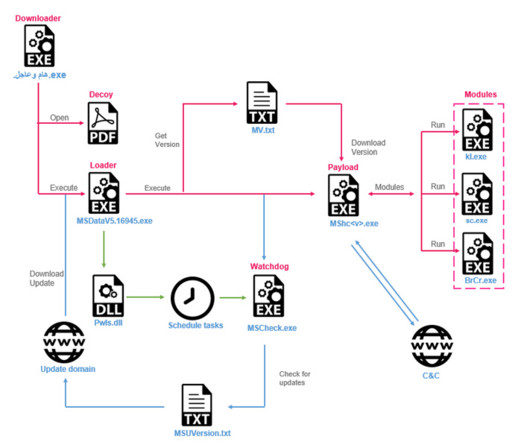
Kaspersky is reporting a zero-click iOS exploit in the wild: Mobile device backups contain a partial copy of the filesystem, including some of the user data and service databases. The timestamps of the files, folders and the database records allow to roughly reconstruct the events happening to the device. The mvt-ios utility produces a sorted timeline of events into a file called “timeline.csv,” similar to a super-timeline used by conventional digital forensic tools.










































Let's personalize your content