Patch ‘Em or Weep: Study Reveals Most Vulnerable IoT, Connected Assets
Tech Republic Security
SEPTEMBER 7, 2023
Phones, tablets and workstations with unpatched CVEs are a clear and present danger. New Armis study lists the most vulnerable.
Tech Republic Security
SEPTEMBER 7, 2023
Phones, tablets and workstations with unpatched CVEs are a clear and present danger. New Armis study lists the most vulnerable.

Bleeping Computer
SEPTEMBER 7, 2023
Citizen Lab says two zero-days fixed by Apple today in emergency security updates were actively abused as part of a zero-click exploit chain (dubbed BLASTPASS) to deploy NSO Group's Pegasus commercial spyware onto fully patched iPhones. [.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Graham Cluley
SEPTEMBER 7, 2023
A Texas court has heard how last month a gang of men used a Raspberry Pi device to steal thousands of dollars from ATMs. Read more in my article on the Tripwire State of Security blog.

Anton on Security
SEPTEMBER 7, 2023
Detection Engineering is Painful — and It Shouldn’t Be (Part 1) This blog series was written jointly with Amine Besson, Principal Cyber Engineer, Behemoth CyberDefence and one more anonymous collaborator. This post is our first installment in the “Threats into Detections — The DNA of Detection Engineering” series, where we explore opportunities and shortcomings in the brand new world of Detection Engineering.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Malwarebytes
SEPTEMBER 7, 2023
An investigation by Microsoft has finally revealed how China-based hackers circumvented the protections of a "highly isolated and restricted production environment" in May 2023 to unlock sensitive email accounts belonging to US government agencies. The attack was first reported by Microsoft in July , in an article that left some important questions unanswered.

Bleeping Computer
SEPTEMBER 7, 2023
Google announced today that it is bringing additional security to the Google Chrome standard Safe Browsing feature by enabling real-time phishing protection for all users. [.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Bleeping Computer
SEPTEMBER 7, 2023
State-backed hacking groups have breached a U.S. aeronautical organization using exploits targeting critical Zoho and Fortinet vulnerabilities, a joint advisory published by CISA, the FBI, and the United States Cyber Command (USCYBERCOM) revealed on Thursday. [.
The Hacker News
SEPTEMBER 7, 2023
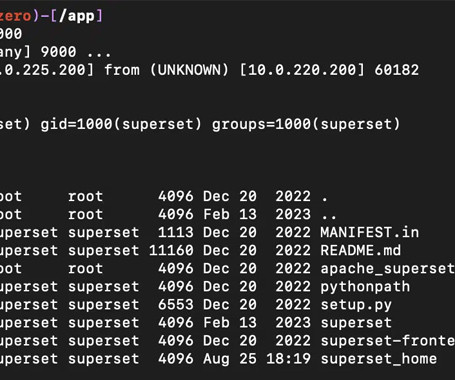
Patches have been released to address two new security vulnerabilities in Apache Superset that could be exploited by an attacker to gain remote code execution on affected systems. The update (version 2.1.1) plugs CVE-2023-39265 and CVE-2023-37941, which make it possible to conduct nefarious actions once a bad actor is able to gain control of Superset’s metadata database.

Security Affairs
SEPTEMBER 7, 2023
Apple rolled out emergency security updates to address two new actively exploited zero-day vulnerabilities impacting iPhones and Macs. The two Apple zero-day vulnerabilities, tracked as CVE-2023-41064 and CVE-2023-41061, reside in the Image I/O and Wallet frameworks. CVE-2023-41064 is a buffer overflow issue that was reported by researchers from researchers at Citizen Lab.

eSecurity Planet
SEPTEMBER 7, 2023
Much like the rest of technology, merger and acquisition (M&A) activity for cybersecurity companies has been in a slump this year. There are a number of reasons why that won’t last, but still, the decline has been noteworthy. For the first seven months of this year, there were a mere 34 startups that got acquired, according to data from Crunchbase.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.
The Hacker News
SEPTEMBER 7, 2023
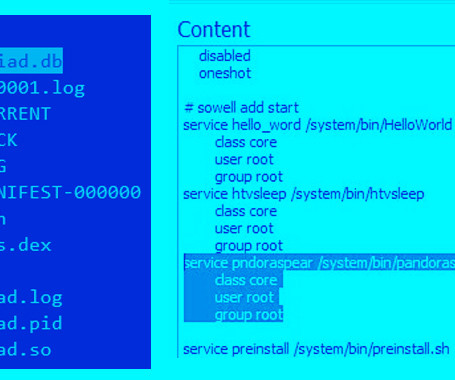
A Mirai botnet variant called Pandora has been observed infiltrating inexpensive Android-based TV sets and TV boxes and using them as part of a botnet to perform distributed denial-of-service (DDoS) attacks. Doctor Web said the compromises are likely to occur either during malicious firmware updates or when applications for viewing pirated video content are installed.

Security Affairs
SEPTEMBER 7, 2023
Citizen Lab reported that the actively exploited zero-days fixed by Apple are being used in Pegasus spyware attacks Researchers at Citizen Lab reported that the actively exploited zero-day flaws (CVE-2023-41064 and CVE-2023-41061) fixed by Apple are being used to infect devices with NSO Group ’s Pegasus spyware. According to the researchers, the two vulnerabilities were chained as part of a zero-click exploit, named BLASTPASS, used in attacks on iPhones running the latest version of iOS (16.6).

WIRED Threat Level
SEPTEMBER 7, 2023
And the first case on the docket may well be Russia’s cyberattacks against civilian critical infrastructure in Ukraine.
Security Affairs
SEPTEMBER 7, 2023
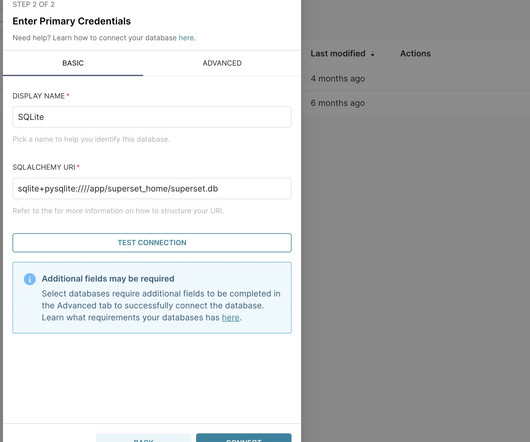
A couple of security vulnerabilities in Apache SuperSet could be exploited by an attacker to gain remote code execution on vulnerable systems. Apache Superset is an open-source Data Visualization and Data Exploration Platform, it is written in Python and based on the Flask web framework. Version 2.1.1 addressed two vulnerabilities, respectively tracked as CVE-2023-39265 and CVE-2023-37941 , that could be exploited to take control of Superset’s metadata database.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.
The Hacker News
SEPTEMBER 7, 2023
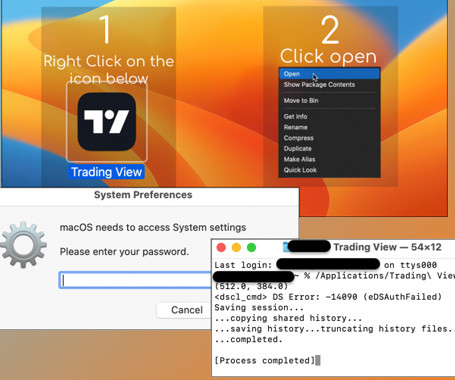
A new malvertising campaign has been observed distributing an updated version of a macOS stealer malware called Atomic Stealer (or AMOS), indicating that it’s being actively maintained by its author. An off-the-shelf Golang malware available for $1,000 per month, Atomic Stealer first came to light in April 2023.
Security Affairs
SEPTEMBER 7, 2023
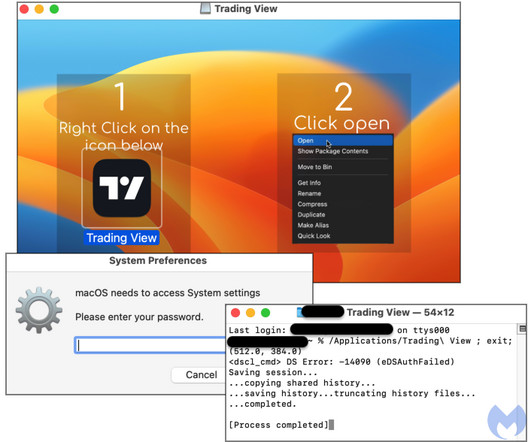
Researchers spotted a new malvertising campaign targeting Mac users with a new version of the macOS stealer Atomic Stealer. Malwarebytes researchers have observed a new malvertising campaign distributing an updated version of the popular Atomic Stealer (AMOS) for Mac. The Atomic Stealer first appeared in the threat landscape in April 2023. In April Cyble Research and Intelligence Labs (CRIL) discovered a Telegram channel advertising a new information-stealing malware, named Atomic macOS Stealer

The Hacker News
SEPTEMBER 7, 2023
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday warned that multiple nation-state actors are exploiting security flaws in Fortinet FortiOS SSL-VPN and Zoho ManageEngine ServiceDesk Plus to gain unauthorized access and establish persistence on compromised systems.

WIRED Threat Level
SEPTEMBER 7, 2023
Here's how to request that your personal information not be used to train Meta's AI model. "Request" is the operative word here.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Heimadal Security
SEPTEMBER 7, 2023
ASUS routers have come under the spotlight due to three critical remote code execution vulnerabilities. These vulnerabilities pose a significant threat, with all three receiving a CVSS v3.1 score of 9.8 out of 10.0. They can be exploited remotely and without authentication, potentially leading to remote code execution, service interruptions, and unauthorized operations on the […] The post Vulnerabilities Uncovered: Critical Remote Code Execution Risks in ASUS Routers appeared first on Heim

Digital Guardian
SEPTEMBER 7, 2023
You've heard of the CCPA but what are the costs of noncompliance? We answer those questions and look at how organizations can use a DLP solution to help facilitate CCPA compliance in this blog.

Dark Reading
SEPTEMBER 7, 2023
Securities and Exchange Commission rules elevate cybersecurity to a critical strategic concern and compel businesses to prioritize cyber resilience.

Bleeping Computer
SEPTEMBER 7, 2023
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added to its catalog of known exploited vulnerabilities (KEV) a critical-severity issue tracked as CVE-2023-33246 that affects Apache's RocketMQ distributed messaging and streaming platform. [.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

Dark Reading
SEPTEMBER 7, 2023
Researchers at Citizen Lab recommend immediately updating any iPhones and iPads to the latest OSes.

Bleeping Computer
SEPTEMBER 7, 2023
A critical vulnerability impacting the Cisco BroadWorks Application Delivery Platform and Cisco BroadWorks Xtended Services Platform could allow remote attackers to forge credentials and bypass authentication. [.

Dark Reading
SEPTEMBER 7, 2023
Attackers use legitimate Windows installer to hide malicious scripts that install a backdoor and miners that leverage victims' graphics processing power.

Bleeping Computer
SEPTEMBER 7, 2023
Microsoft says North Korean hacking groups have breached multiple Russian government and defense targets since the start of the year. [.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Dark Reading
SEPTEMBER 7, 2023
Putting the top 10 generative AI tools to the ethical test reveals more about humanity than artificial intelligence.

Bleeping Computer
SEPTEMBER 7, 2023
Cybercriminals are abusing Google Looker Studio to create counterfeit cryptocurrency phishing websites that phish digital asset holders, leading to account takeovers and financial losses. [.

Dark Reading
SEPTEMBER 7, 2023
This time, they're creating elaborate impostor profiles and using a fresh zero-day and a fake Windows tool to lure in the suspecting.

WIRED Threat Level
SEPTEMBER 7, 2023
Authorities have sanctioned 11 alleged members of the cybercriminal groups, while the US Justice Department unsealed three federal indictments against nine people accused of being members.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content