On Passkey Usability
Schneier on Security
FEBRUARY 12, 2024
Matt Burgess tries to only use passkeys. The results are mixed.

Schneier on Security
FEBRUARY 12, 2024
Matt Burgess tries to only use passkeys. The results are mixed.

Tech Republic Security
FEBRUARY 12, 2024
Google Cloud’s Director of Office of the CISO Nick Godfrey reminds business leaders to integrate security into conversations around financial and business targets.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Malwarebytes
FEBRUARY 12, 2024
The Federal Communications Commission (FCC) has announced that calls made with voices generated with the help of Artificial Intelligence (AI) will be considered “artificial” under the Telephone Consumer Protection Act (TCPA). Effective immediately, that makes robocalls that implement voice cloning technology and target consumers illegal. Robocalls are automated phone calls, often associated with scams, which can be a nuisance to individuals and businesses alike.

Trend Micro
FEBRUARY 12, 2024
The APT group Water Hydra has been exploiting the zero-day Microsoft Defender SmartScreen vulnerability (CVE-2024-21412) in its campaigns targeting financial market traders. This vulnerability, which has now been patched by Microsoft, was discovered and disclosed by the Trend Micro Zero Day Initiative.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Tech Republic Security
FEBRUARY 12, 2024
Read our comprehensive review of Perimeter 81 VPN. Discover its features, pricing, security measures and more to determine if it's the right VPN for you.

Bleeping Computer
FEBRUARY 12, 2024
Hackers are exploiting a server-side request forgery (SSRF) vulnerability in Ivanti Connect Secure, Policy Secure, and ZTA gateways to deploy the new DSLog backdoor on vulnerable devices. [.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Bleeping Computer
FEBRUARY 12, 2024
Bank of America is warning customers of a data breach exposing their personal information after one of its service providers was hacked last year. [.

Security Affairs
FEBRUARY 12, 2024
Exploring the Risks: Unveiling 9 Potential Techniques Hackers Employ to Exploit Public Wi-Fi and Compromise Your Sensitive Data We’ve all used public Wi-Fi: it’s convenient, saves our data, and speeds up browsing. But while we enjoy its benefits, hackers do too. Here, we’ll explore how cybercriminals exploit public Wi-Fi to access your private data and possibly steal your identity.

Bleeping Computer
FEBRUARY 12, 2024
Starting March 13th, telecommunications companies must report data breaches impacting customers' personally identifiable information within 30 days, as required by FCC's updated data breach reporting requirements. [.

Security Boulevard
FEBRUARY 12, 2024
When sensitive information becomes available to outside sources, you have a data leak on your hands. Data leaks are real threats that are easy to ignore. But across all the places your company stores and moves data, it’s only a matter of time until an accidental exposure of information will put your business at risk. […] The post What is a Data Leak?

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

WIRED Threat Level
FEBRUARY 12, 2024
Top congressional lawmakers are meeting in private to discuss the future of a widely unpopular surveillance program, worrying members devoted to reforming Section 702.

Bleeping Computer
FEBRUARY 12, 2024
A phishing campaign detected in late November 2023 has compromised hundreds of user accounts in dozens of Microsoft Azure environments, including those of senior executives. [.

Security Affairs
FEBRUARY 12, 2024
U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Roundcube Webmail Persistent Cross-Site Scripting (XSS) Vulnerability to its Known Exploited Vulnerabilities catalog. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added a Roundcube Webmail Persistent Cross-Site Scripting (XSS) vulnerability, tracked as CVE-2023-43770 , to its Known Exploited Vulnerabilities (KEV) catalog.

Graham Cluley
FEBRUARY 12, 2024
A simple-to-avoid security flaw allowed unauthorised parties to track the location of anyone wearing Livall ski and biking helmets, and listen to group conversations. Read more in my article on the Hot for Security blog.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Security Boulevard
FEBRUARY 12, 2024
Ah, Valentine's Day—the time when love is in the air, and scam artists are ready to swoop in with their own version of a love story. Imagine this: you're swiping through a dating app, hoping to find the yin to your yang, only to find yourself entangled in a web of deception. The post A Valentine’s warning about heartbreak hackers appeared first on Security Boulevard.

Graham Cluley
FEBRUARY 12, 2024
Over 20 hospitals in Bucharest have reportedly been impacted by a ransomware attack after cybercriminals targeted an IT service provider. As a consequence medical staff have been forced to use pen-and-paper rather than computer systems.

The Hacker News
FEBRUARY 12, 2024
Threat actors are leveraging a recently disclosed security flaw impacting Ivanti Connect Secure, Policy Secure, and ZTA gateways to deploy a backdoor codenamed DSLog on susceptible devices. That's according to findings from Orange Cyberdefense, which said it observed the exploitation of CVE-2024-21893 within hours of the public release of the proof-the-concept (PoC) code.

Security Boulevard
FEBRUARY 12, 2024
Zero-trust architecture is rapidly becoming the go-to approach for security and IT leaders to secure voice, mobile and 5G networks and applications. The post Applying Zero-Trust to Voice Networks and the 5G Core appeared first on Security Boulevard.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

The Hacker News
FEBRUARY 12, 2024
When it comes to access security, one recommendation stands out above the rest: multi-factor authentication (MFA). With passwords alone being simple work for hackers, MFA provides an essential layer of protection against breaches. However, it's important to remember that MFA isn't foolproof. It can be bypassed, and it often is.

Bleeping Computer
FEBRUARY 12, 2024
The FBI dismantled the Warzone RAT malware operation, seizing infrastructure and arresting two individuals associated with the cybercrime operation. [.

eSecurity Planet
FEBRUARY 12, 2024
This week saw some repeat products from previous vulnerability recaps, such as Ivanti Policy Secure and JetBrains TeamCity servers. One of the most notable vulnerabilities for this week is Fortinet’s critical FortiOS issue, which affects Fortinet products that use the affected versions of the network operating system. Make sure your security teams consistently check vendor bulletins for vulnerability announcements so your business can stay on top of all threats.

Bleeping Computer
FEBRUARY 12, 2024
At least 18 hospitals in Romania were knocked offline after a ransomware attack took down their healthcare management system. [.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

Security Affairs
FEBRUARY 12, 2024
The Canadian government is going to ban the tool Flipper Zero because it is abused by crooks to steal vehicles in the country. The Canadian government announced that it plans to ban the tool Flipper Zero , and similar hacking devices, to curb the surge in car thefts. Flipper Zero is a portable multi-tool for pentesters and geeks in a toy-like body. It allows hacking digital stuff, such as radio protocols, access control systems, hardware, and more, reads the official website.

Digital Guardian
FEBRUARY 12, 2024
Data infrastructure - required to manage, store, and process data - can take many forms. We look at the different types, aspects, and provide tips on how to build a robust data infrastructure in today's blog.
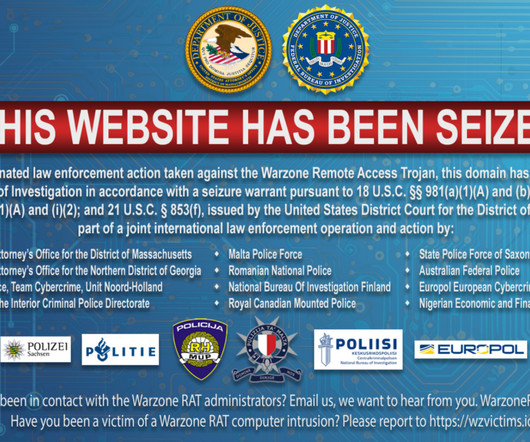
Security Affairs
FEBRUARY 12, 2024
The U.S. Justice Department (DoJ) seized the infrastructure that was used to sell the remote access trojan (RAT) Warzone RAT. The Justice Department announced the seizure of internet domains used to sell the remote access Trojan Warzone RAT (www.warzone[.]ws). The seizure is the result of an international law enforcement operation, federal authorities in Atlanta and Boston charged individuals in Malta and Nigeria, for their involvement in selling the malware.

Bleeping Computer
FEBRUARY 12, 2024
South Korean researchers have publicly disclosed an encryption flaw in the Rhysida ransomware encryptor, allowing the creation of a Windows decryptor to recover files for free. [.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?
Security Boulevard
FEBRUARY 12, 2024
The post Single Sign-On with Fortra IdP appeared first on Digital Defense. The post Single Sign-On with Fortra IdP appeared first on Security Boulevard.

Bleeping Computer
FEBRUARY 12, 2024
Microsoft is testing a new "Automatic Super Resolution" AI-assisted upscaling feature that increases the video and image quality of supported games while also making them run more smoothly. [.

The Hacker News
FEBRUARY 12, 2024
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added a medium-severity security flaw impacting Roundcube email software to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The issue, tracked as CVE-2023-43770 (CVSS score: 6.

Bleeping Computer
FEBRUARY 12, 2024
CISA warns that a Roundcube email server vulnerability patched in September is now actively exploited in cross-site scripting (XSS) attacks. [.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content