Ransomware: 8 Things That You Must Know
Joseph Steinberg
APRIL 6, 2021
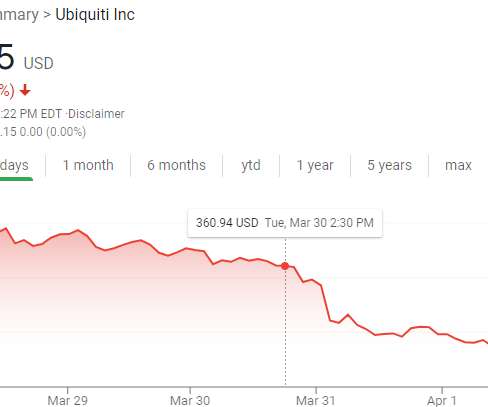
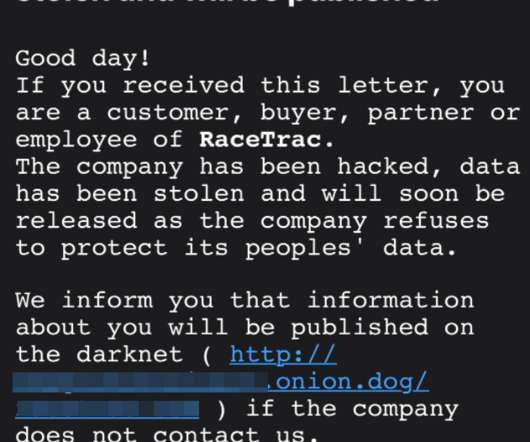
While ransomware may seem like a straightforward concept, people who are otherwise highly-knowledgeable seem to cite erroneous information about ransomware on a regular basis. As such, I would like to point out 8 essential points about ransomware. 1. Paying a demanded ransom may not get you your files back, and may not prevent a leak of your information.







































Let's personalize your content