‘BlueLeaks’ Exposes Files from Hundreds of Police Departments
Krebs on Security
JUNE 21, 2020
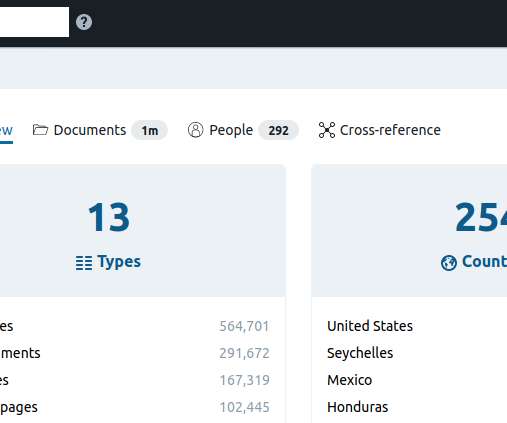
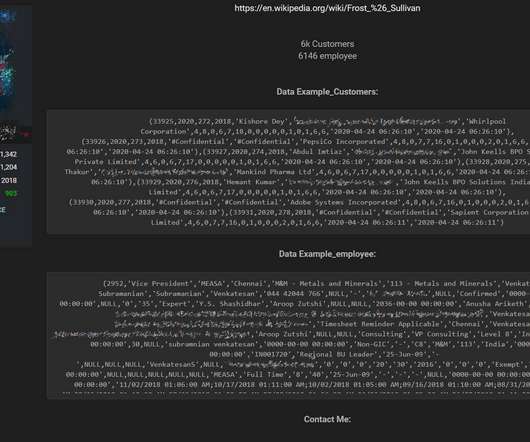
Hundreds of thousands of potentially sensitive files from police departments across the United States were leaked online last week. The collection, dubbed “ BlueLeaks ” and made searchable online, stems from a security breach at a Texas web design and hosting company that maintains a number of state law enforcement data-sharing portals. The collection — nearly 270 gigabytes in total — is the latest release from Distributed Denial of Secrets (DDoSecrets), an alternative to






































Let's personalize your content