Network Firewall vs. Web Application Firewall (WAF)
Security Boulevard
NOVEMBER 1, 2021
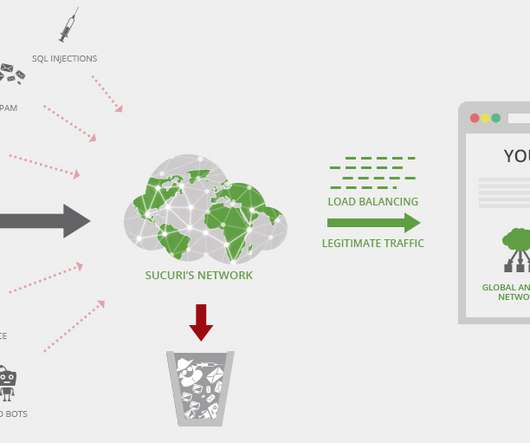
Businesses are taking a closer look at their firewall’s capabilities and considering mixing and matching technologies to cover new security gaps. . Continue reading Network Firewall vs. Web Application Firewall (WAF) at Sucuri Blog.


















































Let's personalize your content