Samsung Encryption Flaw
Schneier on Security
MARCH 4, 2022
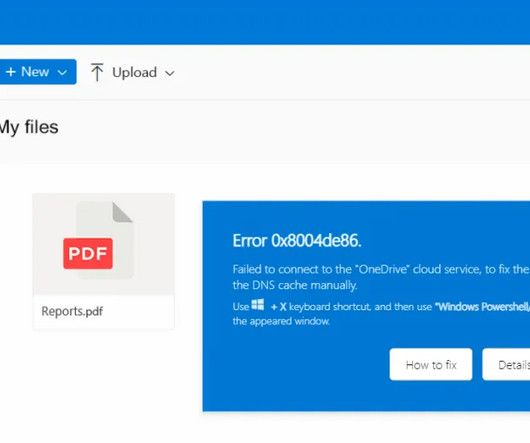
Researchers have found a major encryption flaw in 100 million Samsung Galaxy phones. We reversed-engineered and provide a detailed description of the cryptographic design and code structure, and we unveil severe design flaws. This means that for a given application, all key blobs will be encrypted using the same key.






































Let's personalize your content