WhatsApp hack: Meta wins payout over NSO Group spyware
Malwarebytes
MAY 8, 2025
NSO Group reverse engineered WhatsApp’s software and developed its own software and servers to send messages to victims via the WhatsApp service that contained malware.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Malwarebytes
MAY 8, 2025
NSO Group reverse engineered WhatsApp’s software and developed its own software and servers to send messages to victims via the WhatsApp service that contained malware.

Zero Day
JUNE 17, 2025
"The company and its founder have worked with government spy agencies and surveillance industry contractors to surveil mobile phones and track user location," Bloomberg reported. Since SMS lacks the proper encryption, it has never been a safe and secure way to exchange authentication codes or other private information.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

SecureWorld News
APRIL 3, 2025
Then came the inevitable: a ransomware attack that encrypted patient records, forced appointment cancellations for three weeks, and ultimately cost more than $12 million in recovery costs, regulatory fines, and lost revenue. We're not proposing surveillance; we're implementing guardrails that protect everyone while maintaining privacy."

Penetration Testing
JULY 9, 2025
A recent update embeds a persistent backdoor, turning what was once a hit-and-run data thief into a long-term intruder capable of remote command execution, system surveillance, and re-infection. Originally known for its data exfiltration from browser extensions and cold wallets, AMOS now goes beyond theft.

Centraleyes
JUNE 23, 2025
Continuous Monitoring Zero Trust methodology relies on ongoing surveillance of behavior, activity patterns, and access requests. In addition, Surespan integrated augmented reality (AR) headsets from RealWear into their Zero Trust environment, enabling remote technicians to receive real-time guidance from engineers.

SecureList
NOVEMBER 28, 2024
However, P8 contains many built-in functions and redesigns of the communication protocol and encryption algorithm, making it a well-designed and powerful espionage platform. The access management software facilitates access to the encrypted partition of the drive. There are also some changes to the victimology.

Security Affairs
FEBRUARY 9, 2025
CISA adds Microsoft Outlook, Sophos XG Firewall, and other flaws to its Known Exploited Vulnerabilities catalog Cisco addressed two critical flaws in its Identity Services Engine (ISE) Notorious hacker behind 40+ cyberattacks on strategic organizations arrested Lazarus APT targets crypto wallets using cross-platform JavaScript stealer U.S.

Security Affairs
OCTOBER 27, 2024
CISA adds ScienceLogic SL1 flaw to its Known Exploited Vulnerabilities catalog VMware failed to fully address vCenter Server RCE flaw CVE-2024-38812 Cisco states that data published on cybercrime forum was taken from public-facing DevHub environment Internet Archive was breached twice in a month Unknown threat actors exploit Roundcube Webmail flaw (..)

Jane Frankland
JANUARY 12, 2025
Double extortion ransomware is now a preferred techniquea devastating one-two punch where attackers not only encrypt a companys data but also steal sensitive information. These groups are also shifting toward more human-centric exploits , like social engineering and insider assistance.

SecureWorld News
JUNE 18, 2025
Model inversion attacks: These aim to reverse-engineer sensitive training data. Although harmless on its own, it highlighted how real systems, like medical imaging or surveillance, could be tricked to make critical misidentifications, simply by adding crafted noise to inputs. Amazingly, this was done with only $50 of API queries.

Zero Day
JUNE 27, 2025
Best-in-class features for secure online browsing The IVPN app uses the best encryption standards currently (AES 256-bit with perfect forward secrecy and ChaCha20-Poly 1305), as well as post-quantum cryptography. For example, you can connect to a US server via a UK server, thereby masking your IP address and getting double encryption.

SecureWorld News
MAY 19, 2025
The evolution of cybersecurity in space During the Cold War, surveillance satellites were prominent on both sides, but the lack of internet and networking meant that most of the interference revolved around jamming and intercepting radio signals.

Security Affairs
JULY 21, 2025
The sample analyzed by the mobile security firm maintains its surveillance capabilities, takes control of the microphone and camera, collects data, encrypts it with a C2-sent password, then uploads it via SFTP after further C2 instructions. One fake VPN app posed as Starlink, likely exploiting recent interest. ” concludes.

Schneier on Security
MAY 23, 2024
Despite encryption and local storage, the new feature raises privacy concerns for certain Windows users. This requires an intimacy greater than your search engine, email provider, cloud storage system, or phone. And the incentives of surveillance capitalism are just too much to resist.

SC Magazine
MARCH 10, 2021
A hacking collective compromised roughly 150,000 internet-connected surveillance cameras from Verkada, Inc., Hacktivist Tillie Kottmann is reportedly among those asserting responsibility for the incident, telling Bloomberg that their act helped expose the security holes of modern-day surveillance platforms. What did Verkada do wrong?

Schneier on Security
MARCH 13, 2019
And if you read his 3,000-word post carefully, Zuckerberg says nothing about changing Facebook's surveillance capitalism business model. Moreover, Facebook should share any innovative engineering solutions with the world, much as it currently shares its data center engineering. Better security for collected user data.

Schneier on Security
JANUARY 18, 2019
Australia, and elsewhere -- argue that the pervasive use of civilian encryption is hampering their ability to solve crimes and that they need the tech companies to make their systems susceptible to government eavesdropping. Levy and Robinson write: In a world of encrypted services, a potential solution could be to go back a few decades.

Security Boulevard
JANUARY 28, 2022
Compared to OTR (Off-the-Record) which basically allows single-user type of secure and encrypted communication the OMEMO protocol actually allows multi-user type of data and information exchange further strengthening the protocol's position on the market for secure mobile IM (instant messaging) applications.

Schneier on Security
FEBRUARY 21, 2020
Sometime around 1993 or 1994, during the first Crypto Wars, I was part of a group of cryptography experts that went to Washington to advocate for strong encryption. Markey was against forcing encrypted phone providers to implement the NSA's Clipper Chip in their devices, but wanted us to reach a compromise with the FBI regardless.

Schneier on Security
FEBRUARY 6, 2023
But aside from some special cases and unique circumstances, that’s not how encryption systems are exploited in practice. I wrote this in my book, Data and Goliath : The problem is that encryption is just a bunch of math, and math has no agency. This is bulk surveillance and can easily operate on this massive scale.

The Last Watchdog
DECEMBER 31, 2019
All the encryption , firewalls , cryptography, SCADA systems , and other IT security measures would be useless if that were to occur. Muthukrishnan Access control, surveillance , and testing are the three major components that comprise the physical security of a system. Access control is the restricting of access to a system.

SecureWorld News
JUNE 25, 2020
Privacy and security advocates may be forced to battle it out on the Senate floor to stop a newly introduced bill that will help law enforcement get past encryption. New backdoor bill in Congress hits encryption debate head on. The question: should encrypted communication be out of law enforcement's reach?

Krebs on Security
AUGUST 5, 2019
This story is about how crooks increasingly are abusing third-party financial aggregation services like Mint , Plaid , Yodlee , YNAB and others to surveil and drain consumer accounts online. “If the account is active, hackers then can go to the next stage for 2FA phishing or social engineering, or linking the accounts with another.”

The Last Watchdog
MAY 29, 2020
Diquet “It is a ‘mostly de-centralized’ approach, where most of the data never leaves the user’s device, in order to protect the user’s privacy as much as possible,” says Alban Diquet, the head of engineering at Data Theorem , a supplier of application security solutions. And the data is deleted after 14 days.” “The I’ll keep watch.

Schneier on Security
MAY 3, 2019
On one side is law enforcement, which wants to be able to break encryption, to access devices and communications of terrorists and criminals. Pervasive surveillance capitalism -- as practiced by the Internet companies that are already spying on everyone -- matters. Tim Berners-Lee has called them "philosophical engineers."

eSecurity Planet
OCTOBER 8, 2024
Companies like Verizon, AT&T, and Lumen Technologies were targeted in this attack, allowing unauthorized access to critical systems used for court-authorized wiretapping — a tool vital for law enforcement surveillance. law enforcement for surveillance purposes. The hackers, identified by U.S.

Security Affairs
NOVEMBER 24, 2021
Apple has filed suit to ban the Israeli surveillance firm NSO Group and parent company Q Cyber Technologies from using its product and services. federal court for illegally targeting its customers with the surveillance spyware Pegasus. That needs to change,” said Craig Federighi , Apple’s senior vice president of Software Engineering.

The Last Watchdog
OCTOBER 3, 2019
“They may discover their targets through some sort of automated technique, which gets them a toehold into the company, or they might just simply go to Shodan (search engine) to discover open, available RDP hosts ,” Shier told me. They’ll take more manual steps to encrypt servers, exfiltrate data – or do both.
Security Affairs
MARCH 27, 2021
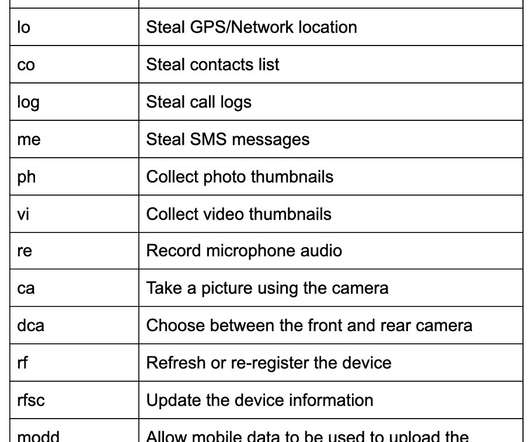
Researchers spotted a sophisticated Android spyware that implements exfiltration capabilities and surveillance features, including recording audio and phone calls. “The “System Update” app was identified by zLabs researchers who noticed an Android application being detected by the z9 malware engine powering zIPS on-device detection.

Security Affairs
SEPTEMBER 1, 2024
Under Meredith Whittaker, It’s Out to Prove Surveillance Capitalism Wrong EU investigating Telegram over user numbers Cryptojacking via CVE-2023-22527: Dissecting a Full-Scale Cryptomining Ecosystem Follow me on Twitter: @securityaffairs and Facebook and Mastodon Pierluigi Paganini ( SecurityAffairs – hacking, newsletter)

Schneier on Security
MARCH 5, 2019
On one side is law enforcement, which wants to be able to break encryption, to access devices and communications of terrorists and criminals. Pervasive surveillance capitalism -- as practiced by the Internet companies that are already spying on everyone -- matters. Tim Berners-Lee has called them "philosophical engineers."
Security Affairs
MAY 20, 2022
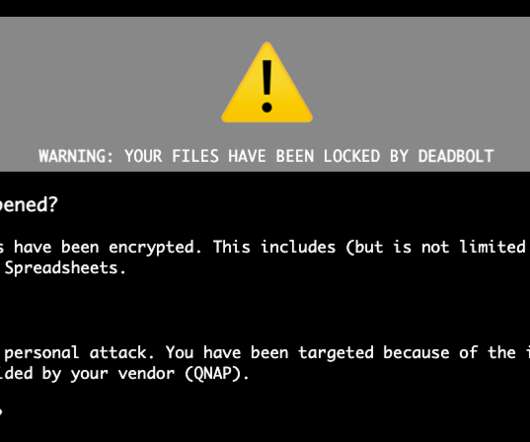
.” Since January, DeadBolt ransomware operators are targeting QNAP NAS devices worldwide , its operators claim the availability of a zero-day exploit that allows them to encrypt the content of the infected systems. Once encrypted the content of the device, the ransomware appends.

Malwarebytes
JULY 4, 2022
DNS encryption. DNS encryption plugs a gap that makes it easy to track the websites you visit. DNS encryption restores your privacy by making it impossible for anything other than the DNS resolver to read and respond to your queries. FIDO2 is a specification that uses public key encryption for authentication.

Malwarebytes
AUGUST 26, 2021
The Bahrain government and groups linked to them—such as LULU , a known operator of Pegasus, and others like them who are associated with a separate government—were tagged as culprits of the surveillance activity. Disabling iMessage also means that your once-encrypted message could be easily intercepted by attackers.

Security Affairs
AUGUST 4, 2019
Sonicwall warns of a spike in the number of attacks involving encrypted malware and IoT malware. million fine for selling flawed surveillance technology to the US Gov. How to Reverse Engineer, Sniff & Bruteforce Vulnerable RF Adult Toys with WHID Elite. Prolific Dark Web dealer of drugs pleads guilty. Cisco to pay $8.6

SecureWorld News
MAY 27, 2020
Because this is such sensitive information, in Mozilla's products we try to minimize how much of it is collected with features such as encrypted sync or enhanced tracking protection. The US Senate voted to renew the USA Freedom Act which authorizes a variety of forms of national surveillance. Ron Wyden and Sen.

Malwarebytes
MAY 9, 2022
The online behemoth has become so much more than a search engine, as it owns and produces hardware like Android phones, Google Pixel phones, Nest thermostats, and FitBit devices, while also operating Google Chrome, Google Mail, Google Calendar, Google Hangouts, YouTube, and Waze. And what about Google? The first suggestion is Fastmail.

SecureWorld News
AUGUST 24, 2022
The infection of a device can be achieved via supply chain attacks, social engineering techniques, or the use of hardware with installed software or firmware. encryption keys, biometric information). At the second phase of the attack, the malicious code collects data from the compromised network. The data can be textual (e.g.,

Security Affairs
JANUARY 10, 2021
The Cyber-attack resulted in a large volume of data to be encrypted including database servers and backup data. In December 2020, Symrise AG confirmed that they were the target of Clop Ransomware attack, when 500GB of their data from over 1000 infected devices was encrypted by cyber criminals. 4securitas.com ). Original Post at [link].
Adam Shostack
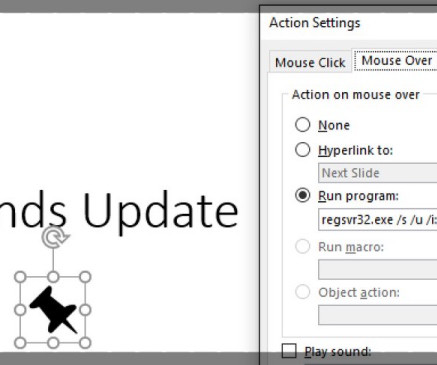
JANUARY 2, 2025
For example: German researchers have discovered security flaws that could let hackers, spies and criminals listen to private phone calls and intercept text messages on a potentially massive scale even when cellular networks are using the most advanced encryption now available. Washington Post, 2014).

Malwarebytes
MARCH 9, 2022
The default search engine in DuckDuckGo. Many sites have a.onion version available to make it even harder to perform surveillance on the user. All traffic between Tor users and onion services is end-to-end encrypted, so you do not need to worry about connecting over HTTPS. That’s not all.

Security Affairs
DECEMBER 2, 2022
Naturally, threat actors follow the trend and exploit the technology for surveillance, payload delivery, kinetic operations, and even diversion. and that Wi-Fi or Radio Frequency (RF) signals used by drone platforms are properly encrypted against eavesdropping or manipulation. free from obstacles, sparsely populated, etc.)

The Last Watchdog
OCTOBER 19, 2021
I highly recommend reading Zuboff’s New York Times Book of the Year, The Age of Surveillance Capitalism: The Fight for A Human Future At the New Frontier of Power as well as viewing Rifkin’s riveting speech, The Third Industrial Revolution: A Radical New Sharing Economy. LW: Is this primarily aimed at enterprises, SMBs or individuals?

CyberSecurity Insiders
JANUARY 20, 2022
MIAMI–( BUSINESS WIRE )–Shareholders entrusted Cloudastructure with $30 million via a RegA+ to expand their cloud-based video surveillance platform empowered with Artificial Intelligence and Machine Learning analytics. As a result of that team’s efforts, Cloudastructure’s video surveillance platform now includes: People Detection.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content