CVE-2024-28064: Critical Flaw Discovered in Totemomail Email Encryption Software
Penetration Testing
MAY 23, 2024
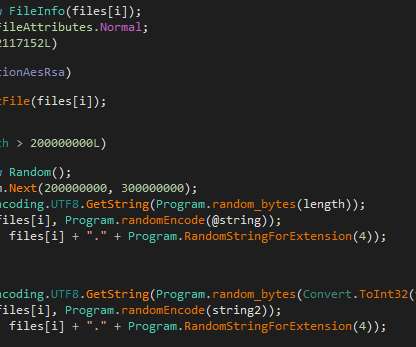
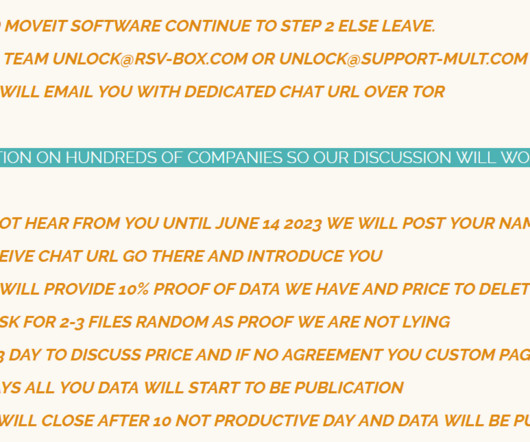
Cybersecurity researchers have uncovered two serious vulnerabilities in Totemomail, a widely used email encryption software now part of Accellion’s Kiteworks platform.













































Let's personalize your content