Attackers use CSS to create evasive phishing messages
Security Affairs
MARCH 17, 2025
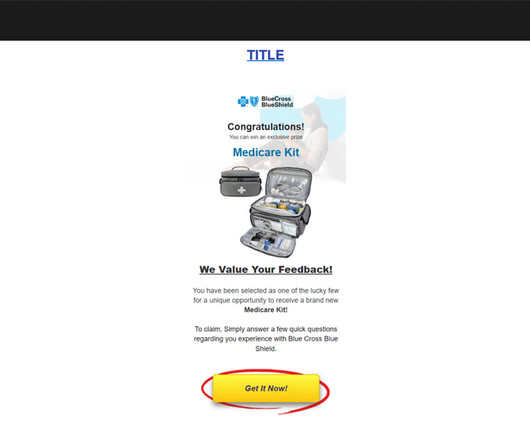
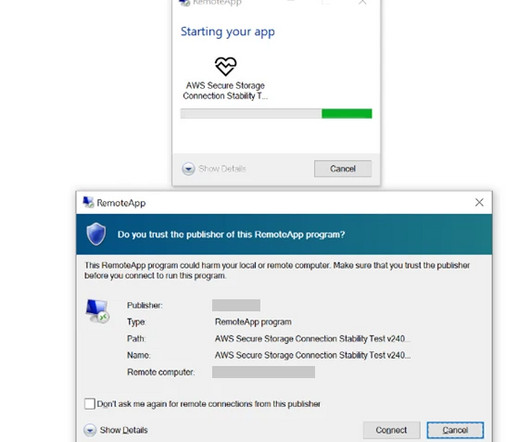
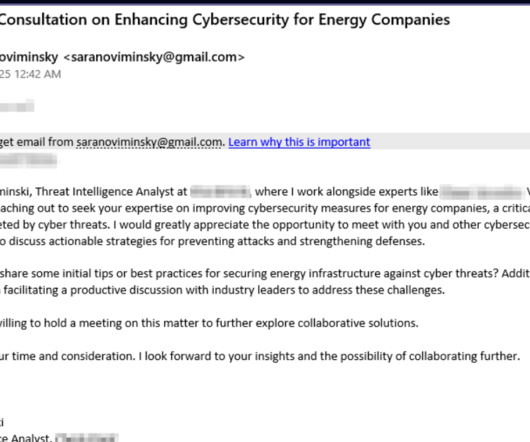
Threat actors exploit Cascading Style Sheets (CSS) to bypass spam filters and detection engines, and track users actions and preferences. Cisco Talos observed threat actors abusing Cascading Style Sheets (CSS) to evade detection and track user behavior, raising security and privacy concerns, including potential fingerprinting.











































Let's personalize your content