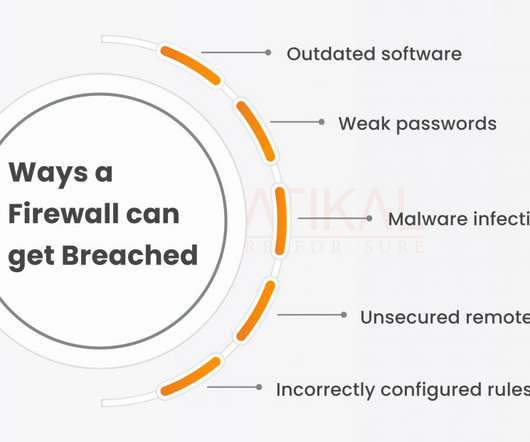
Can Your Firewall Be Hacked? Severe Flaws Found in pfSense
Penetration Testing
MAY 19, 2025
Security researcher Navy Titanium have released a technical deep-dive uncovering three severe vulnerabilities affecting pfSense, the popular open-source The post Can Your Firewall Be Hacked? Severe Flaws Found in pfSense appeared first on Daily CyberSecurity.
















































Let's personalize your content