Mitigating Dynamic Application Risks with Secure Firewall Application Detectors
Cisco Security
SEPTEMBER 23, 2021
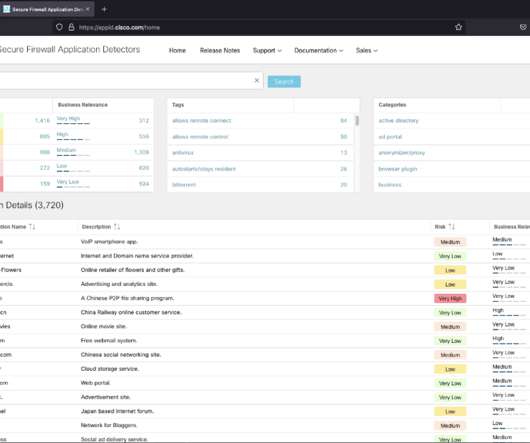
As part of our strategy to enhance application awareness for SecOps practitioners, our new Secure Firewall Application Detectors portal, [link] , provides the latest and most comprehensive application risk information available in the cybersecurity space. This unstoppable dynamic creates blind spots that often increases risk.

















































Let's personalize your content