Apple Calls Out 'Mercenary Spyware' Vendors Enabling State Surveillance
SecureWorld News
APRIL 15, 2024
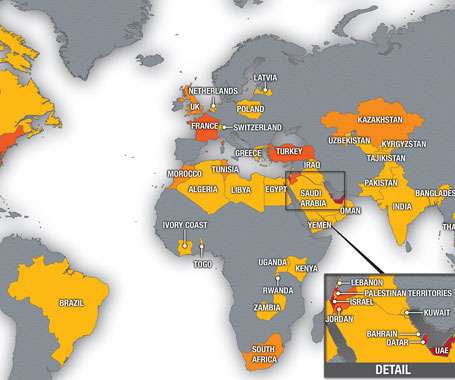
Apple has escalated its fight against the commercial spyware industry enabling state actors to conduct highly-targeted cyberattacks against journalists, activists, politicians, and other high-risk individuals around the world. These types of attacks have victims in every country in the world." Just last month, the U.S.















































Let's personalize your content