Kalay cloud platform flaw exposes millions of IoT devices to hack
Security Affairs
AUGUST 17, 2021
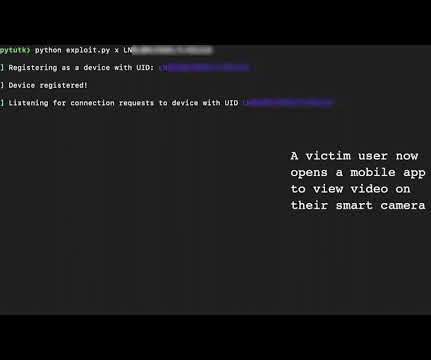
FireEye Mandiant researchers have discovered a critical vulnerability in the Kalay cloud platform that exposes millions of IoT devices to attacks. The flaw could be easily exploited by a remote attacker to take over an IoT device, the only info needed for the attack is the Kalay unique identifier (UID) of the targeted user.
















































Let's personalize your content