The US Capitol Riot is a National Cybersecurity Emergency
Adam Levin
JANUARY 7, 2021
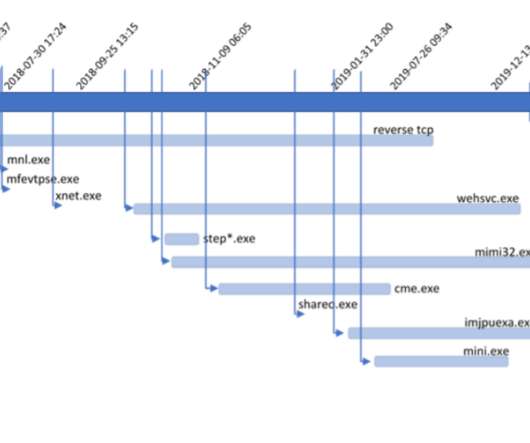
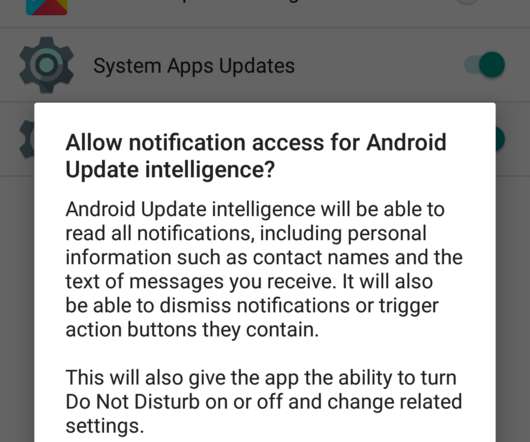
The potentially compromised data could include: Social Security numbers, health records (including mental health), home addresses, phone numbers, etc., as well as details about state business and likely correspondents, which could be used in a spear phishing attack, doxxing , and other social engineering ploys.






























Let's personalize your content